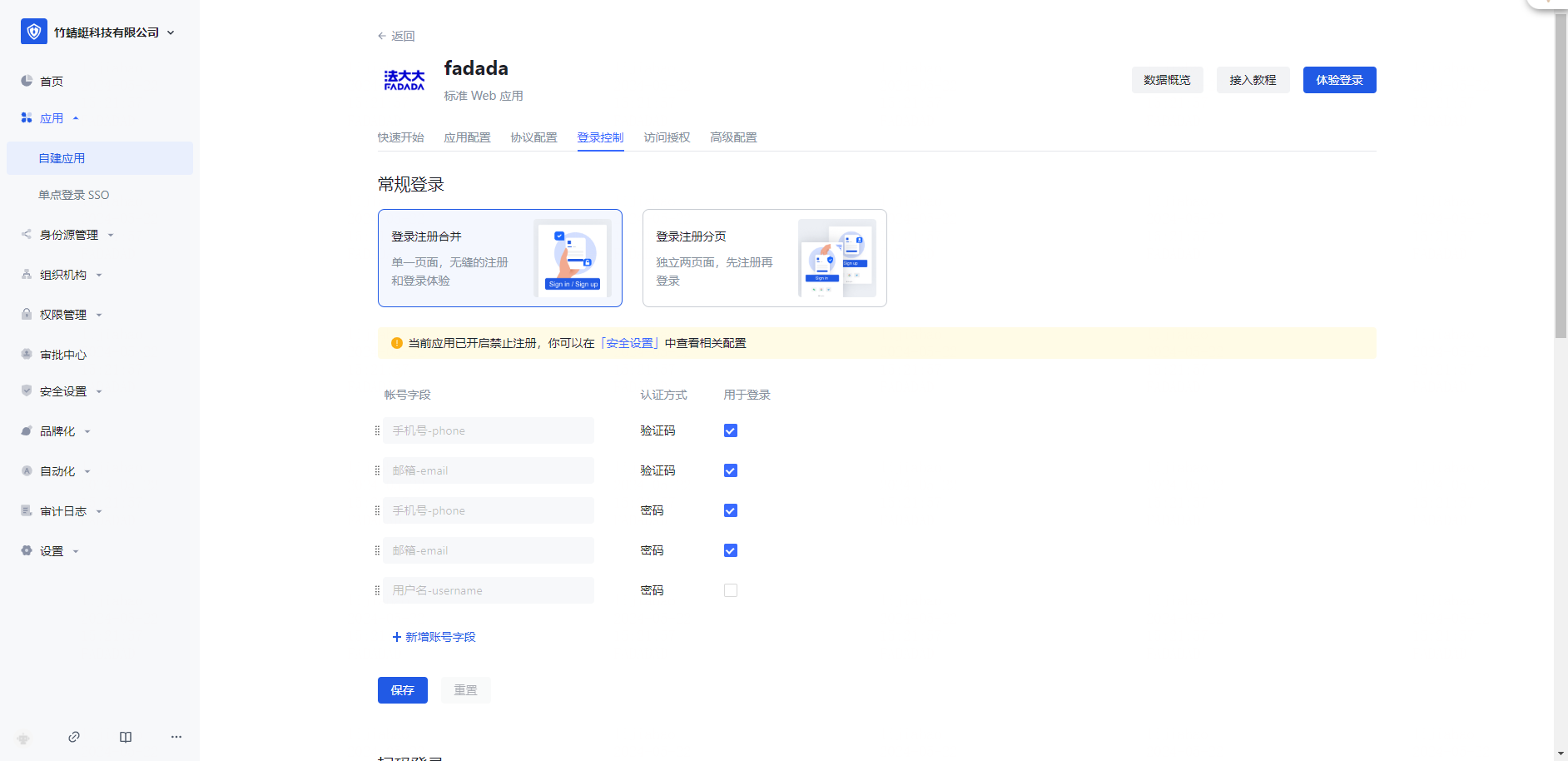
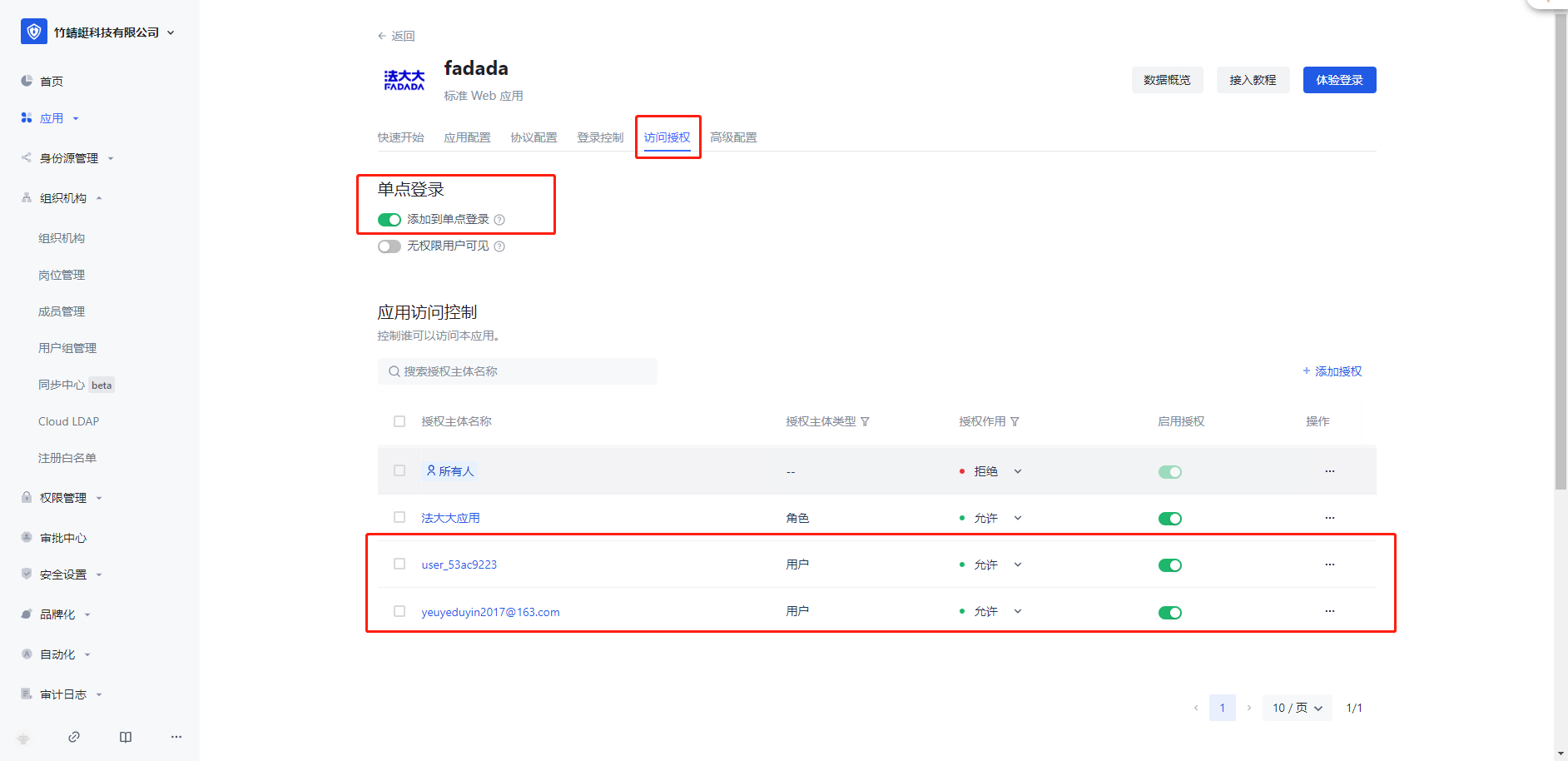
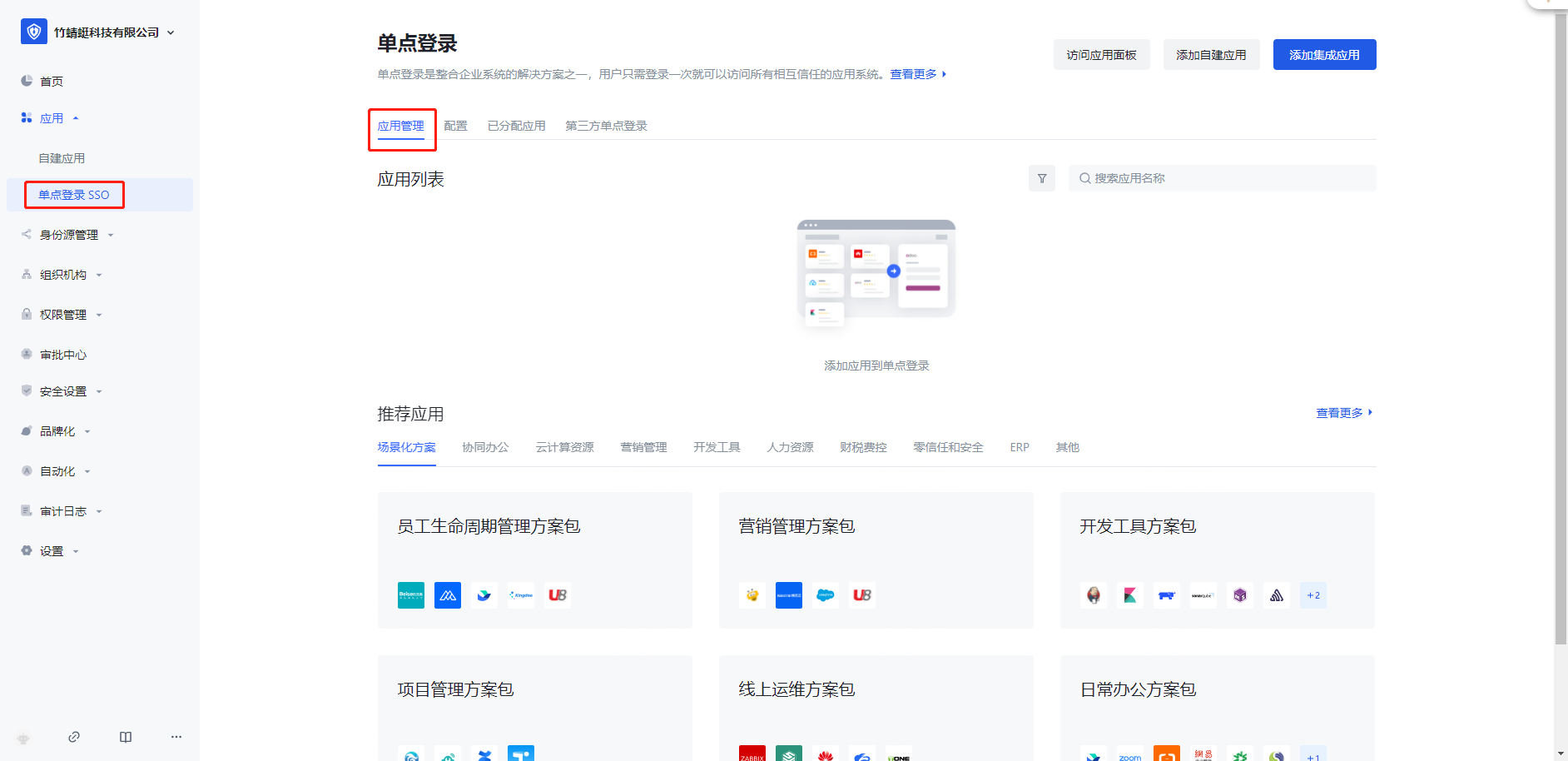
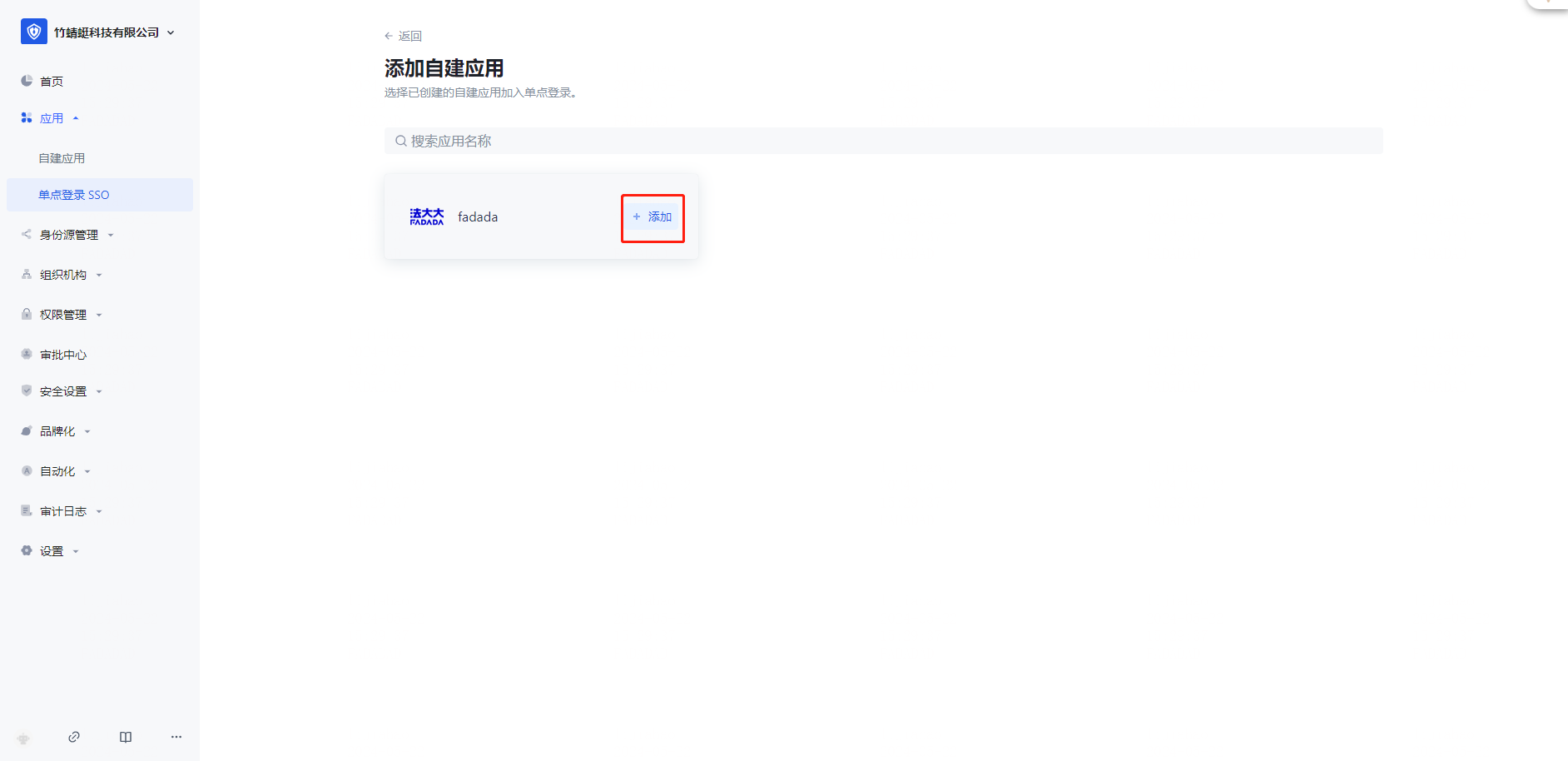
➡️ If you use the method in enterprise wechat/Dingding.com, please go to Enterprise Settings - Integration Management - Third-Party Platform Integration to enable the corresponding configuration, and manage your membership through enterprise wechat/Dingding.com.
Application scenario: Use FASC SaaS method to enhance e-signature capability through single sign-on
Prerequisite for use: has been registered in FASC certification enterprise, and the version is one of the standard version, professional version, and group version
Additional note:
1. Currently, DADA only supports IdP integration based on SAML 2.0 protocol
2. Currently, the login account cannot be automatically synchronized between IdP and SP, and needs to be manually added in the SaaS background of Dada
3. One IdP application corresponds to only one enterprise account. If you need to log in to multiple enterprise accounts, create multiple IdP applications
SMAL2.0 mode implements single sign-on
Related noun interpretation
noun |
explanation |
Service Provider |
Service providers, referred to as SP, such as: Ali Cloud platform, Tencent Cloud platform, AWS platform, these are service providers, also including Fada SaaS |
Identity Provider |
An identity provider (IdP) can send an identity assertion to an SP. In SAML, the identity assertion is an XML Token that identifies a person, such as IDaas, Authing, Microsoft Entra ID, and the IdP developed by a third party |
SAML Request |
When a user cannot be identified, the SP sends a SAML Request to the IdP (via the browser) requesting the IdP to authenticate the user. |
SAML Response |
After receiving the SAML Request, the IdP will pop up the login box to authenticate the user identity. After the user completes the login in the IdP, the SAML IdP will send the user identity assertion to the SP (placed in the form and sent through the browser POST request). |
Browser |
The SP and IdP communicate with each other through browsers |
Flow chart of data interaction between SP, IdP, and browser
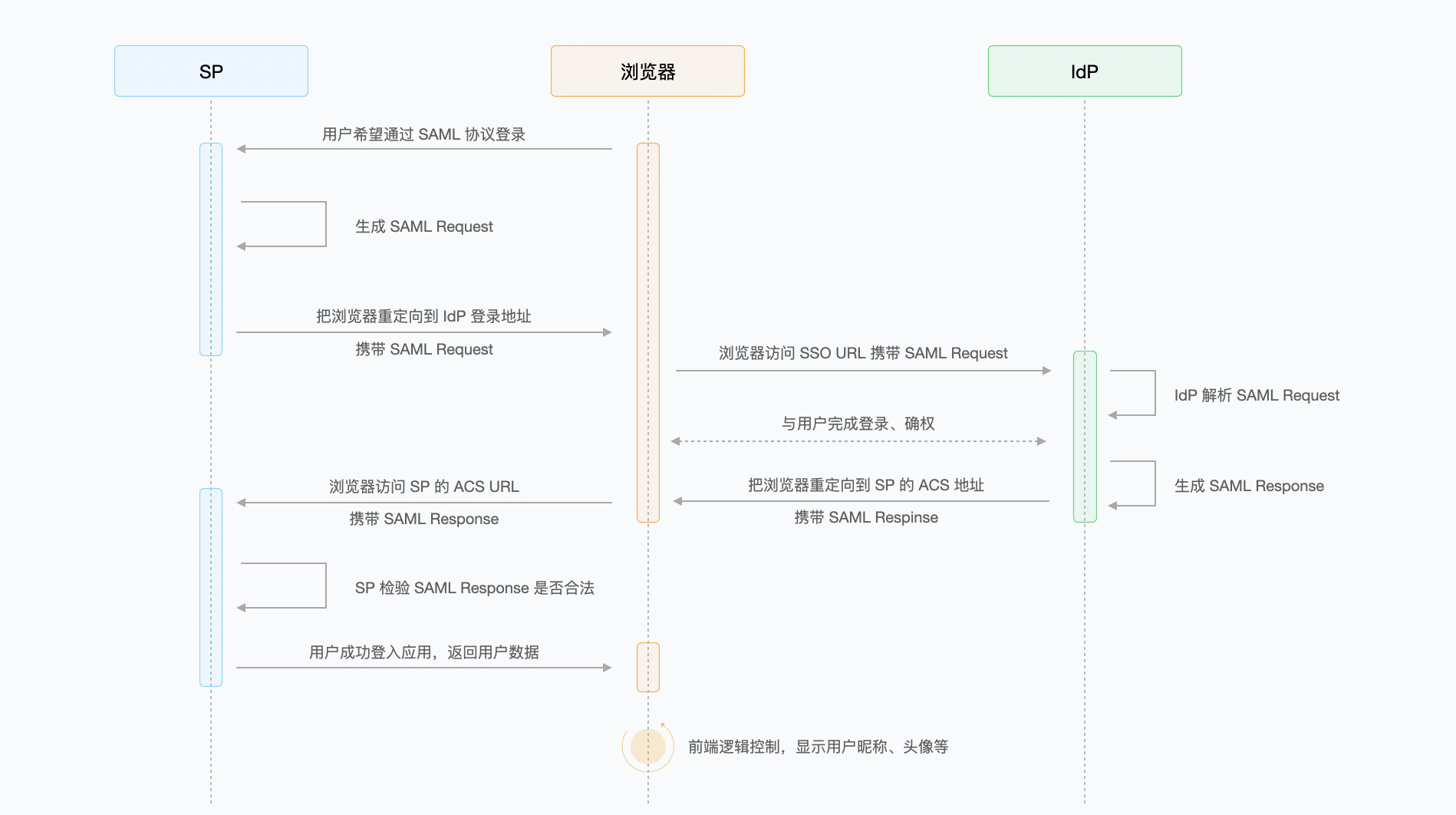
Process description:
1. Users attempt to log in to applications provided by SP (such as Fada SaaS) on their own unified login platform.
2. The SP generates a SAML Request and sends the SAML Request to the IdP through browser redirection.
3. The IdP parses the SAML Request and redirects the user to the authentication page.
4. The user logs in on the login page.
5. The IdP generates a SAML Response and returns a SAML Response to the ACS address of the SP by redirecting the browser, which contains a SAML Assertion for determining the user identity.
6. SP checks the content of the SAML Response.
7. The user successfully logs in to the application provided by the SP.
SAML 2.0 protocol based IdP integration is currently supported, including:
Microsoft Entra ID (formerly Azure Active Directory)
Authing
Alibaba Cloud IDaaS
Okta
Other custom identity sources
Preparatory work
💡 Please ensure that you have the following permissions:
Internal unified account (IdP) management rights
Law Department (SP) administrative authority
Configuration example
1. Example of Microsoft Entra ID operation configuration
1. Implement SSO using Microsoft Entra ID
Microsoft Entra ID (formerly Azure Active Directory) : is a cloud-based identity and access management service that employees can use to access external resources.
Product Address: Create a free Azure account now | Microsoft Azure
Users can use the Microsoft Entra ID to achieve a unified account login, the following is how to use the Microsoft Entra ID unified login method for large SaaS details.
2. Configure the Microsoft Entra ID:
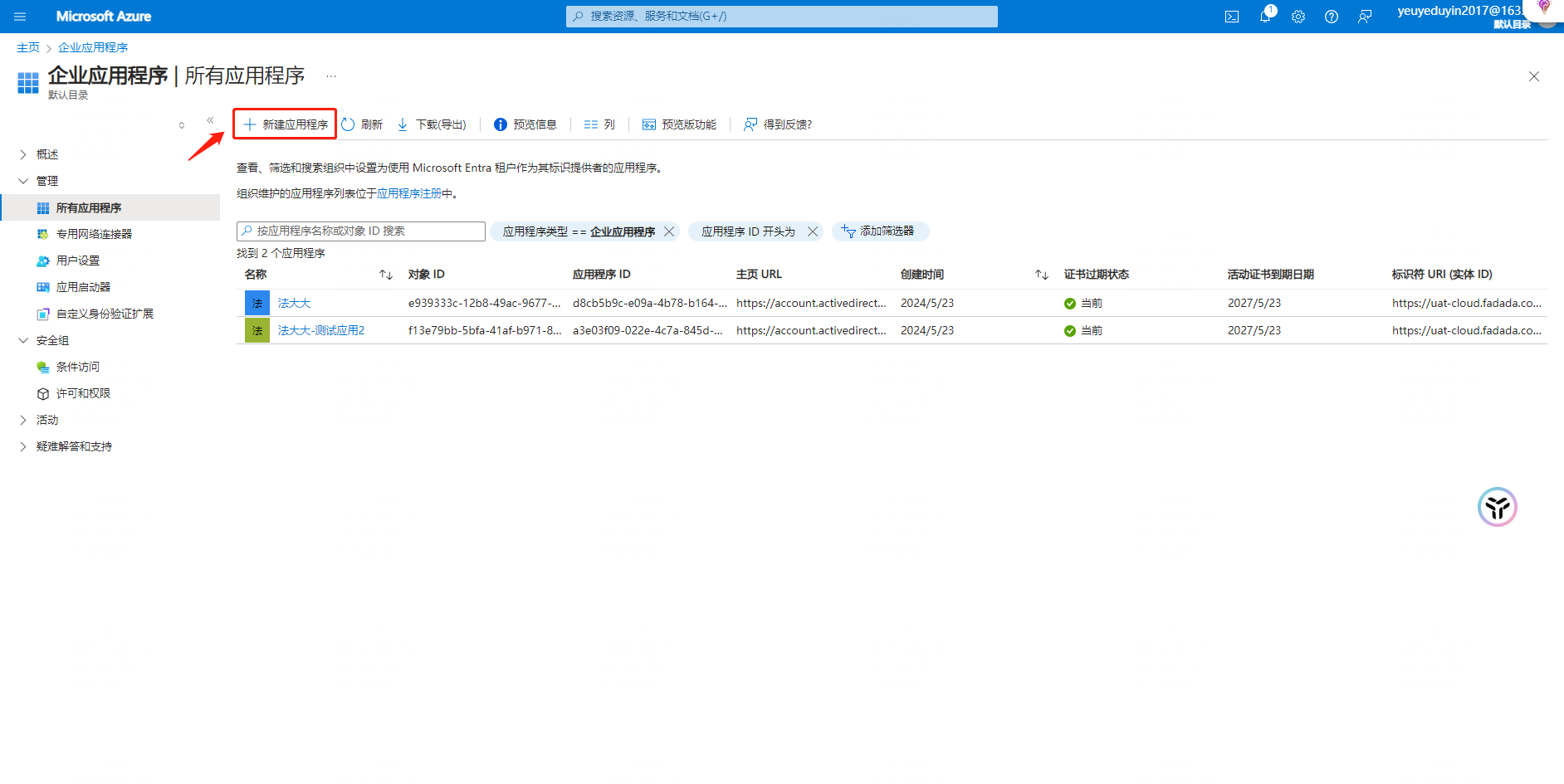
Step 1: Create an application
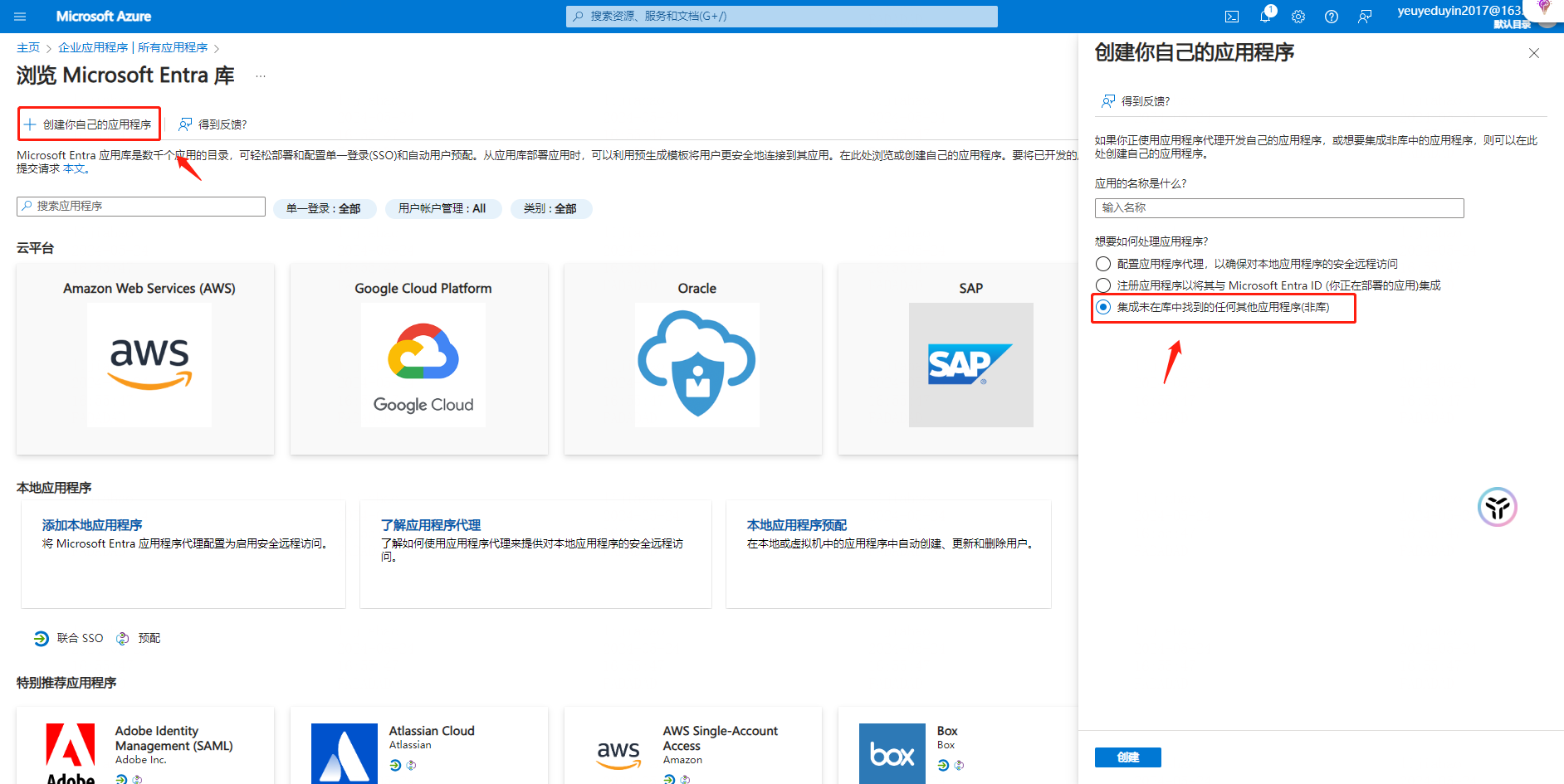
Action 1: Select "Manage" - "Enterprise Application" click "New Application" - "Create your own Application"
Note: User-defined application name (It is recommended to be the same as the name of the enterprise that needs to log in for easy identification)
Step 2 Configure the self-built application
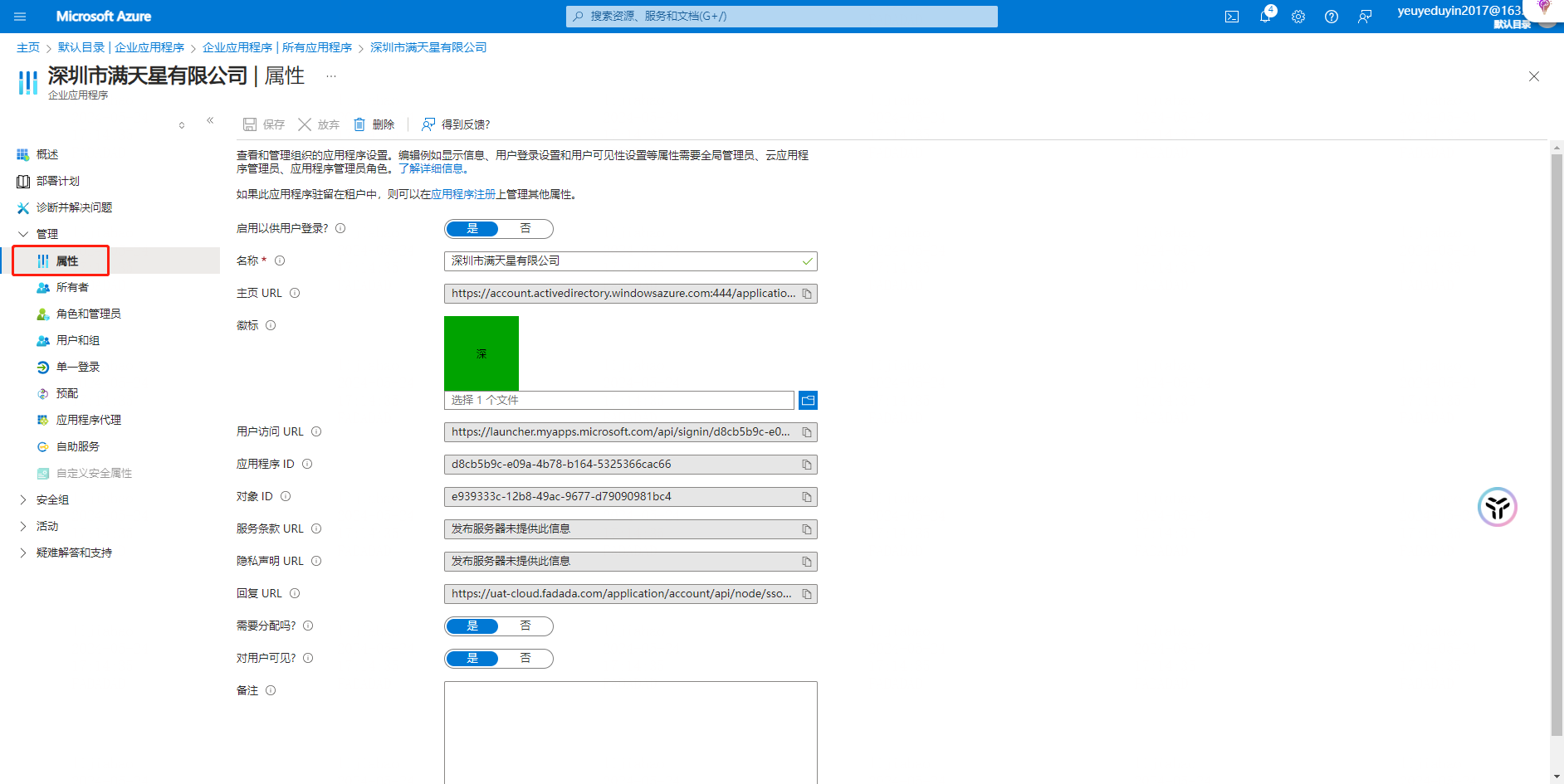
Action: Select 【 Management 】-【 Properties 】
Note: The basic application information can be maintained, and no special requirements are required
Step 3. Configure single login
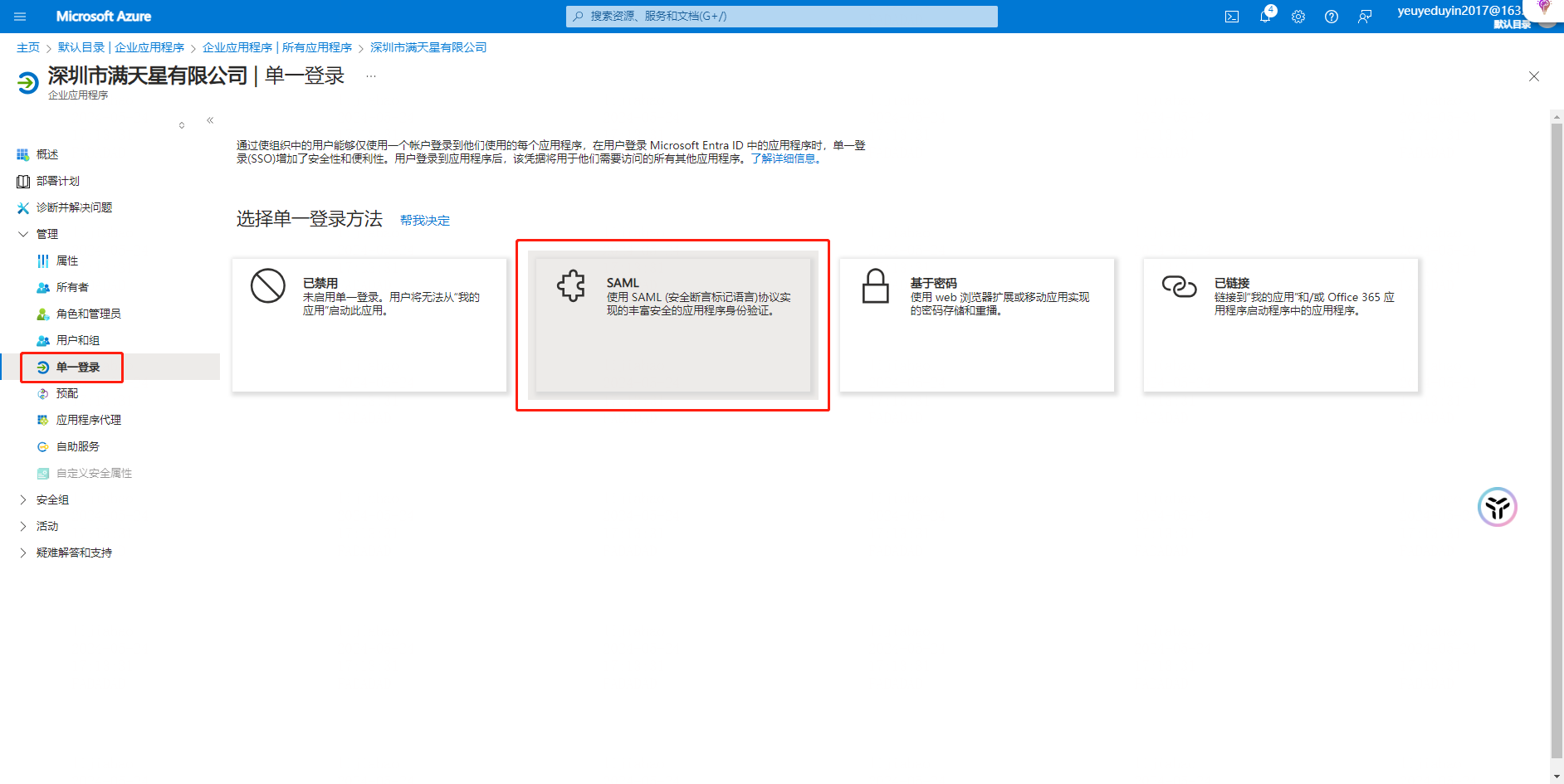
Operation 1: Select 【 Manage 】-【 Single Login 】
Note: Select SAML card and configure SSO using SAML 2.0 protocol
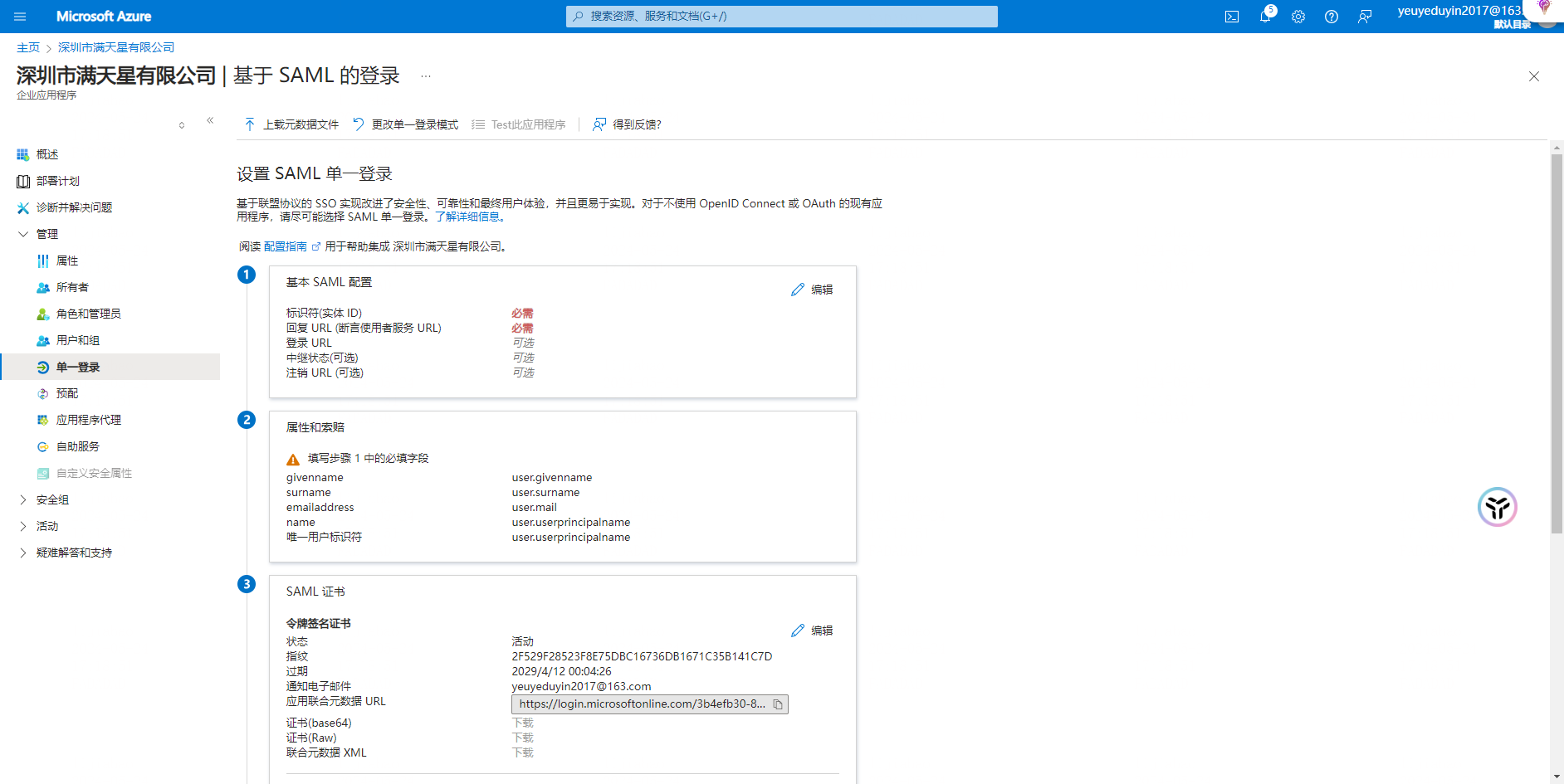
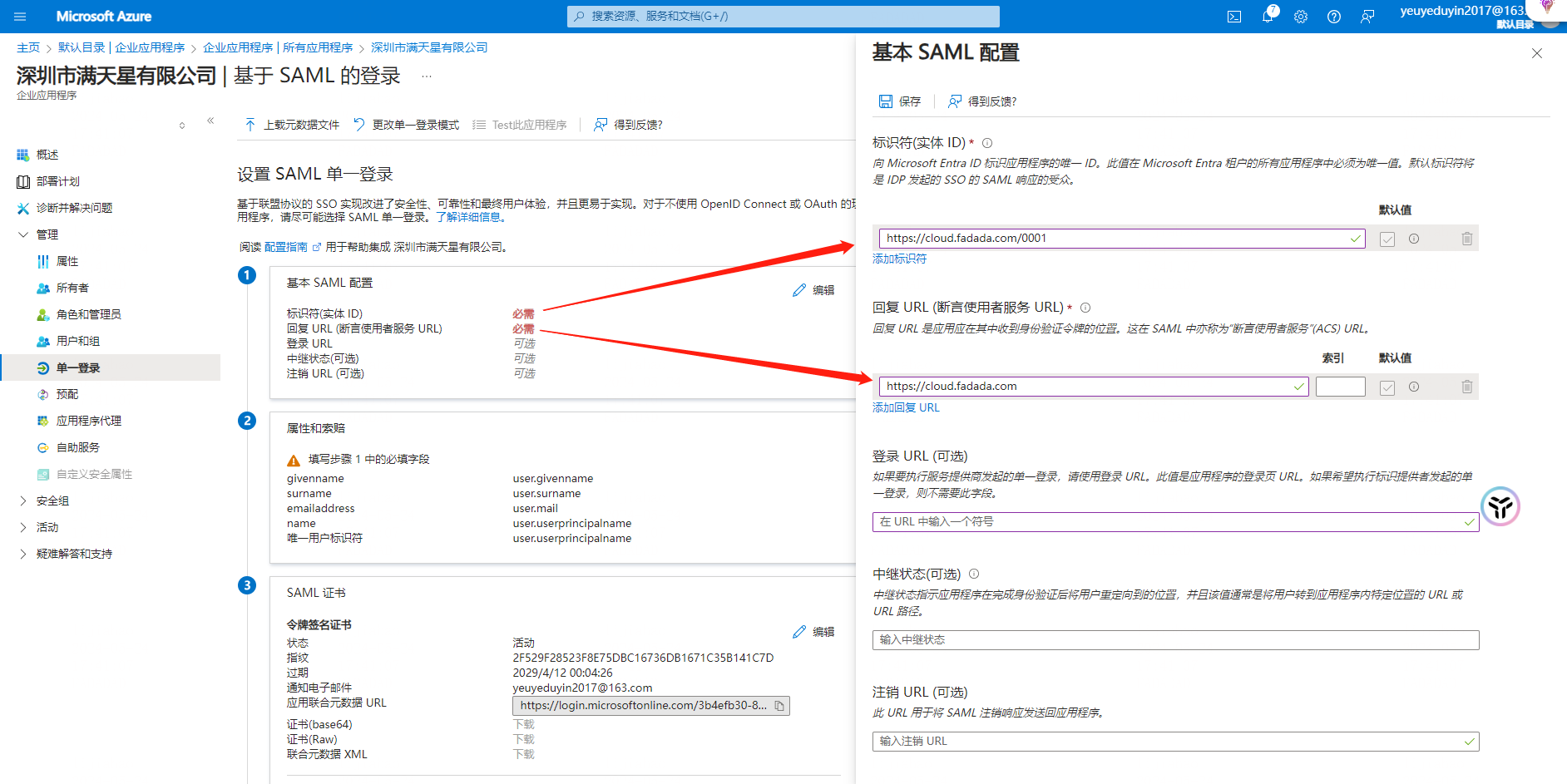
Action 2: 【 Set up SAML Single login 】 - 【 Basic SAML Configuration 】
Note: In the basic SAML configuration, the identifier (entity ID) and the reply URL (assert user service URL) are required parameters, and the first setting can be arbitrarily set a value.
After SSO is configured on the French main end, you need to return to this area to fill in a new one
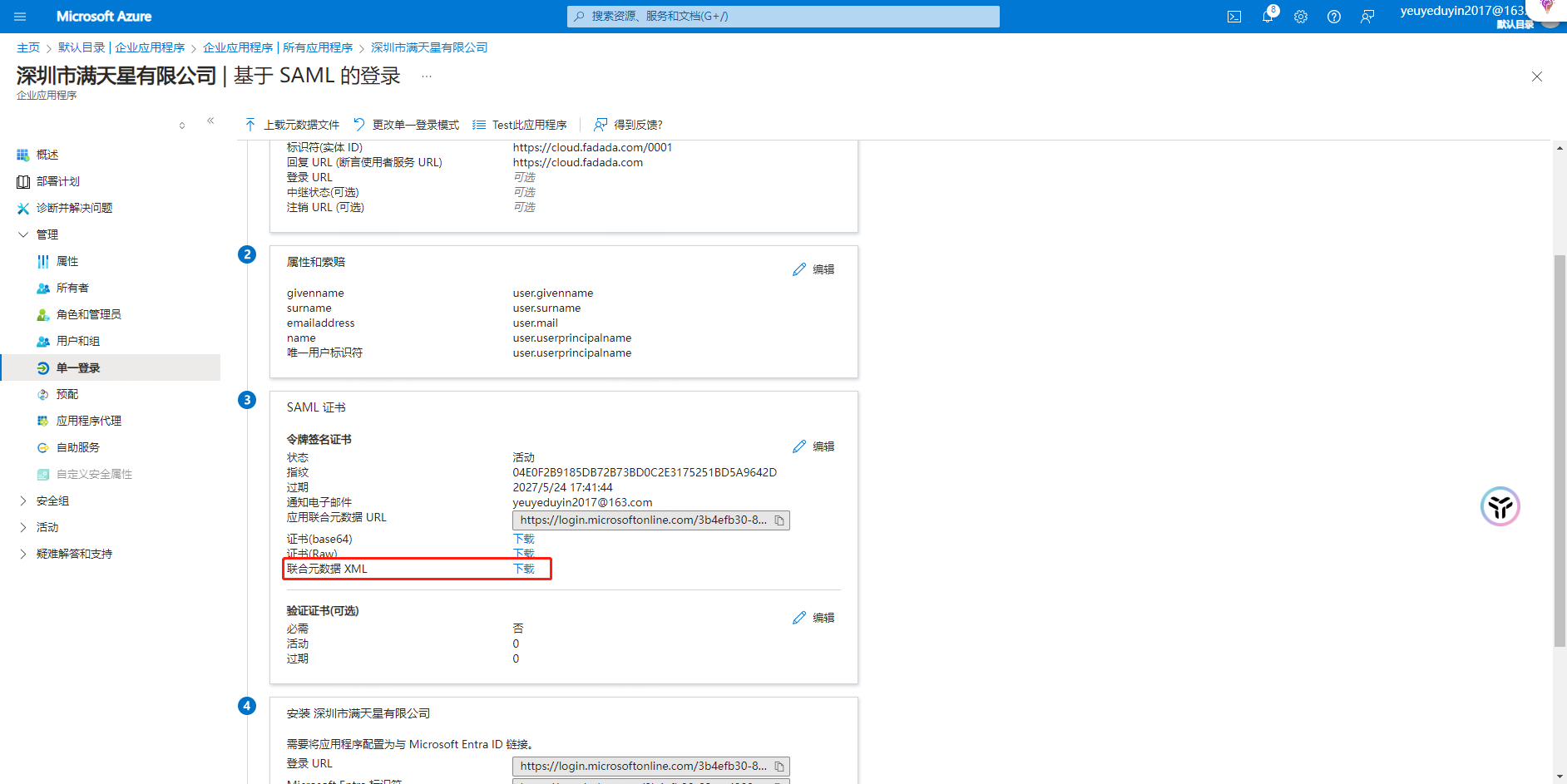
Operation 3: 【 Set SAML Single Login 】 - 【SAML Certificate 】
Note: Need to download federated metadata XML to local computer
The SAML configuration is complete
Step 4: Apply to assign users
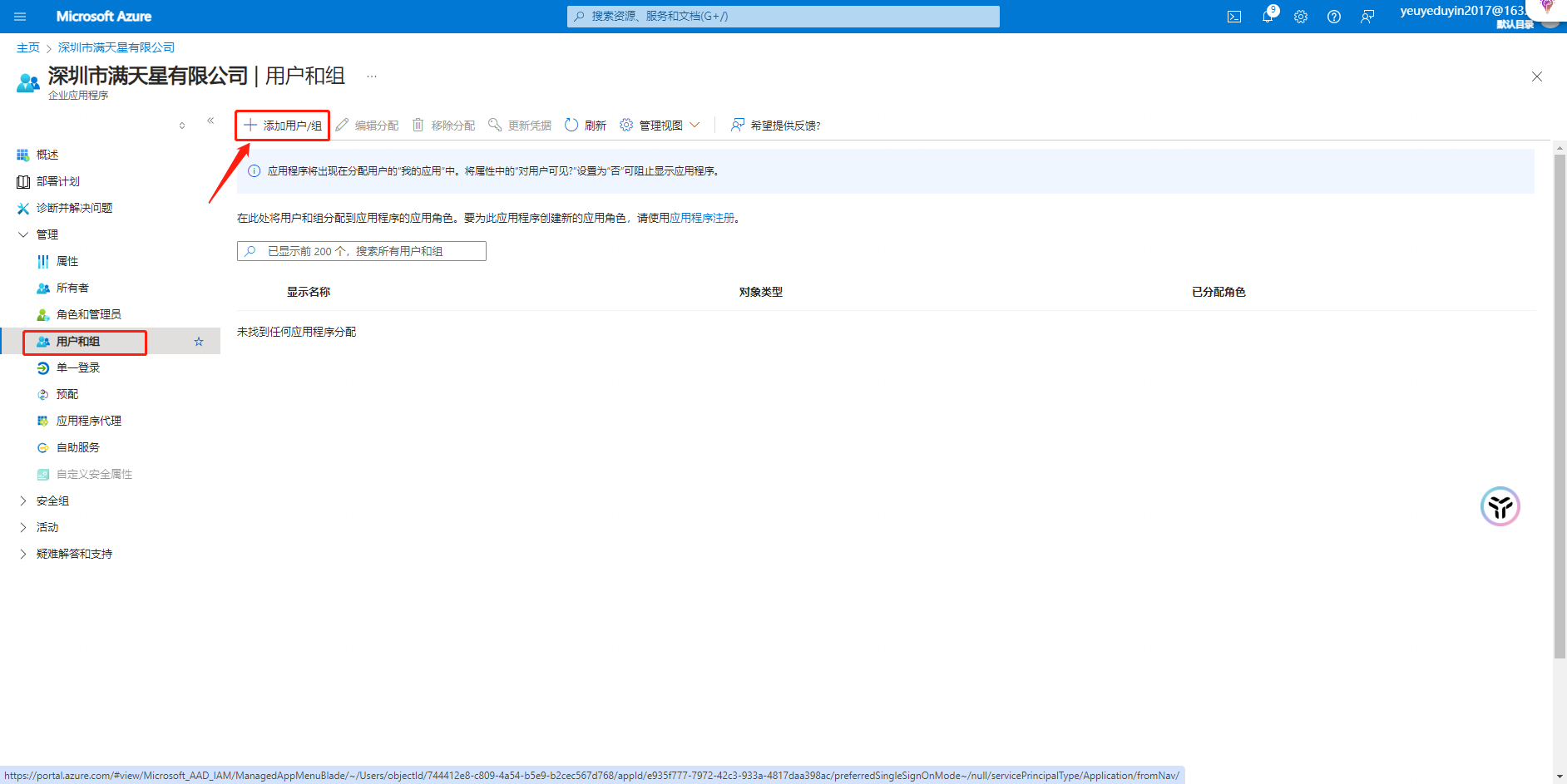
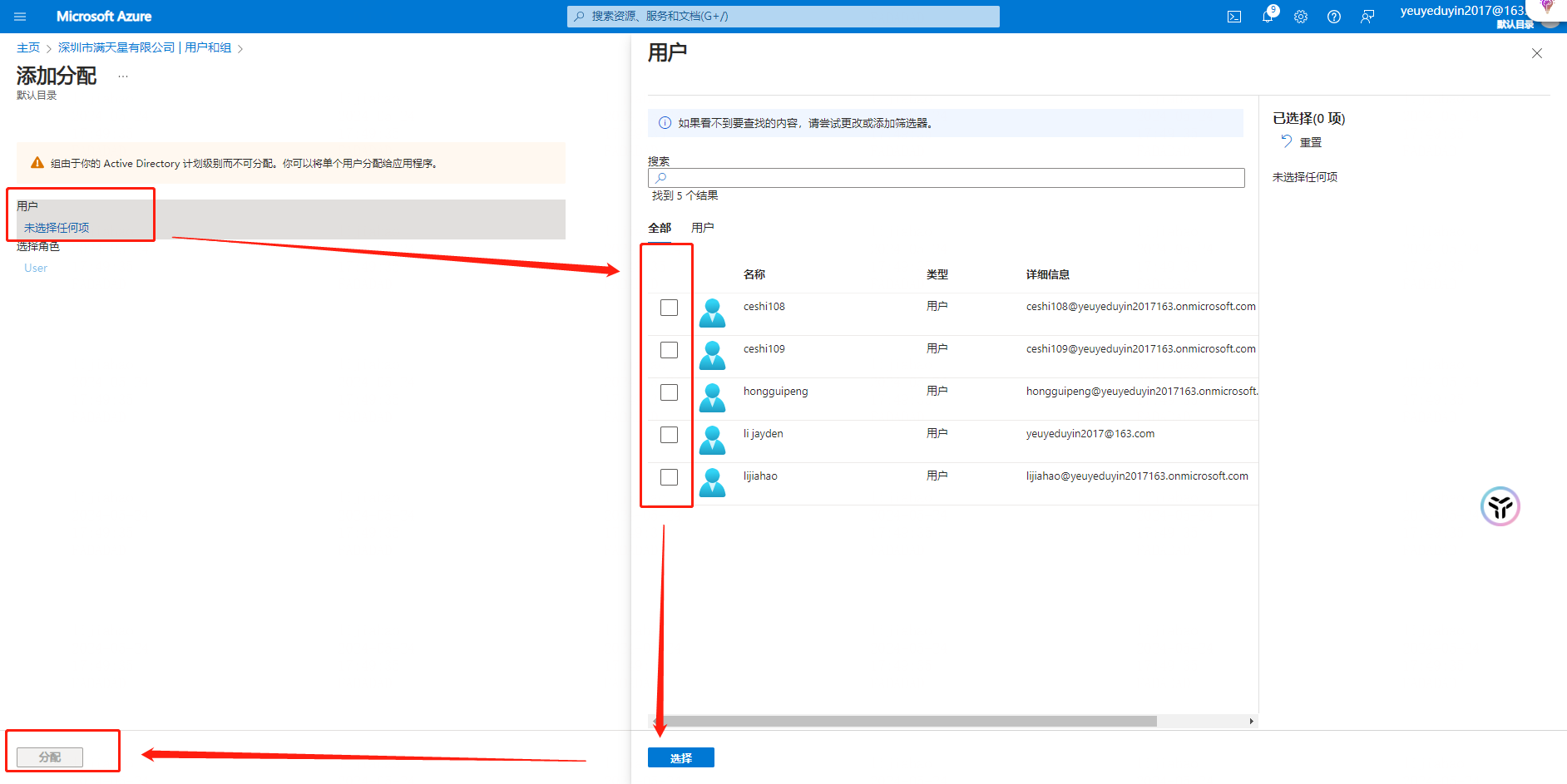
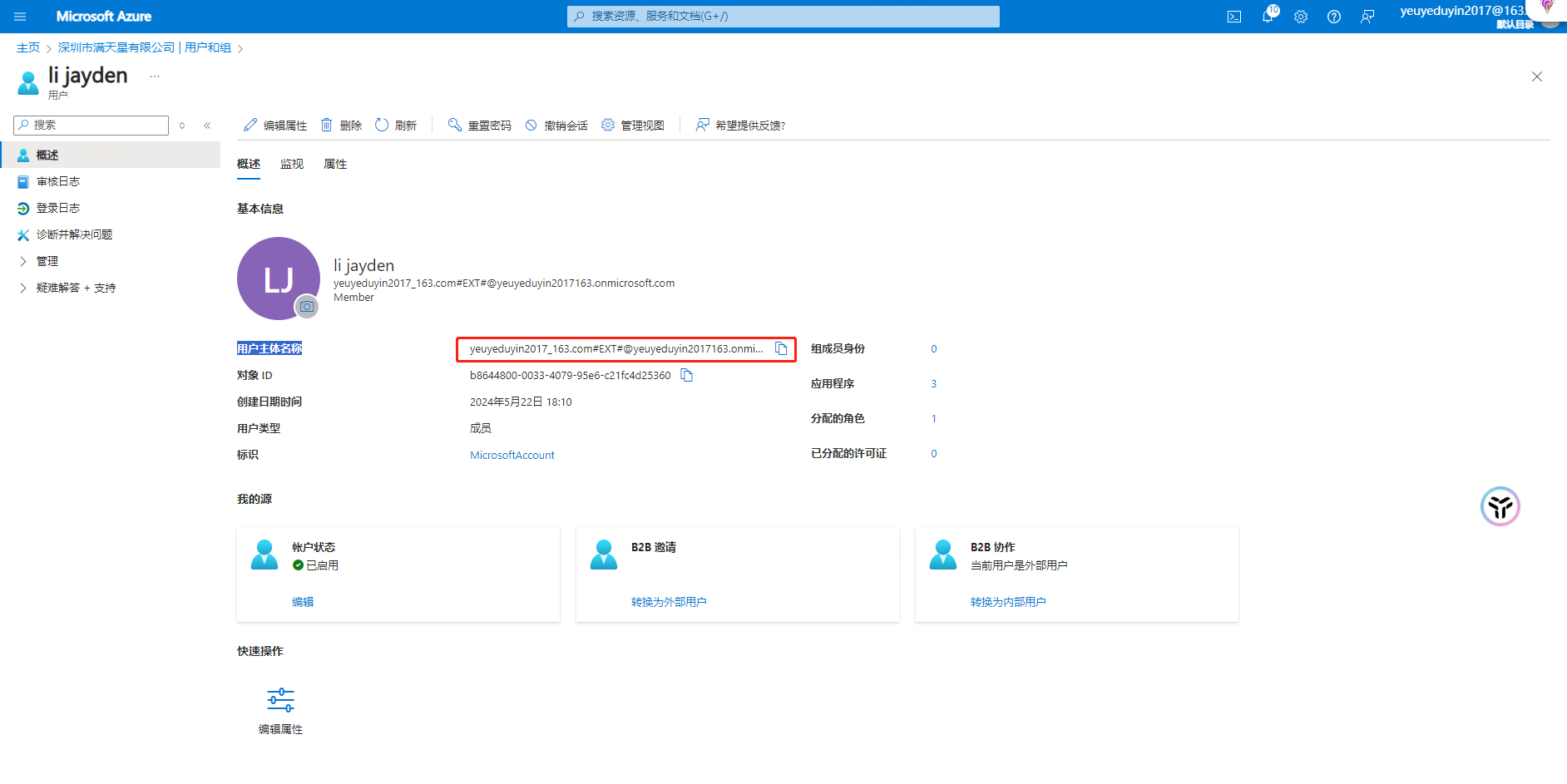
Operation: Select 【 Manage 】-【 Users and Groups 】
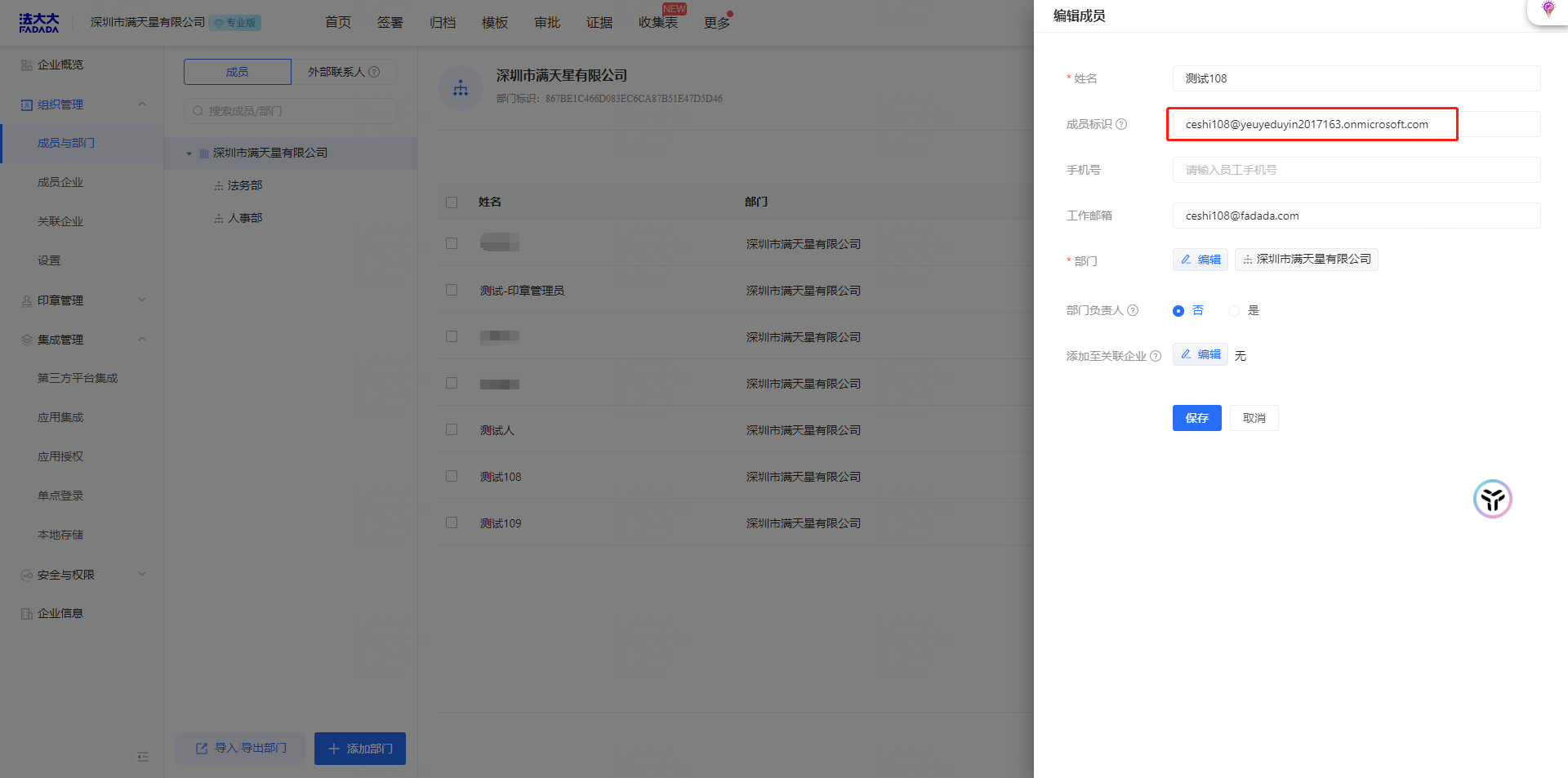
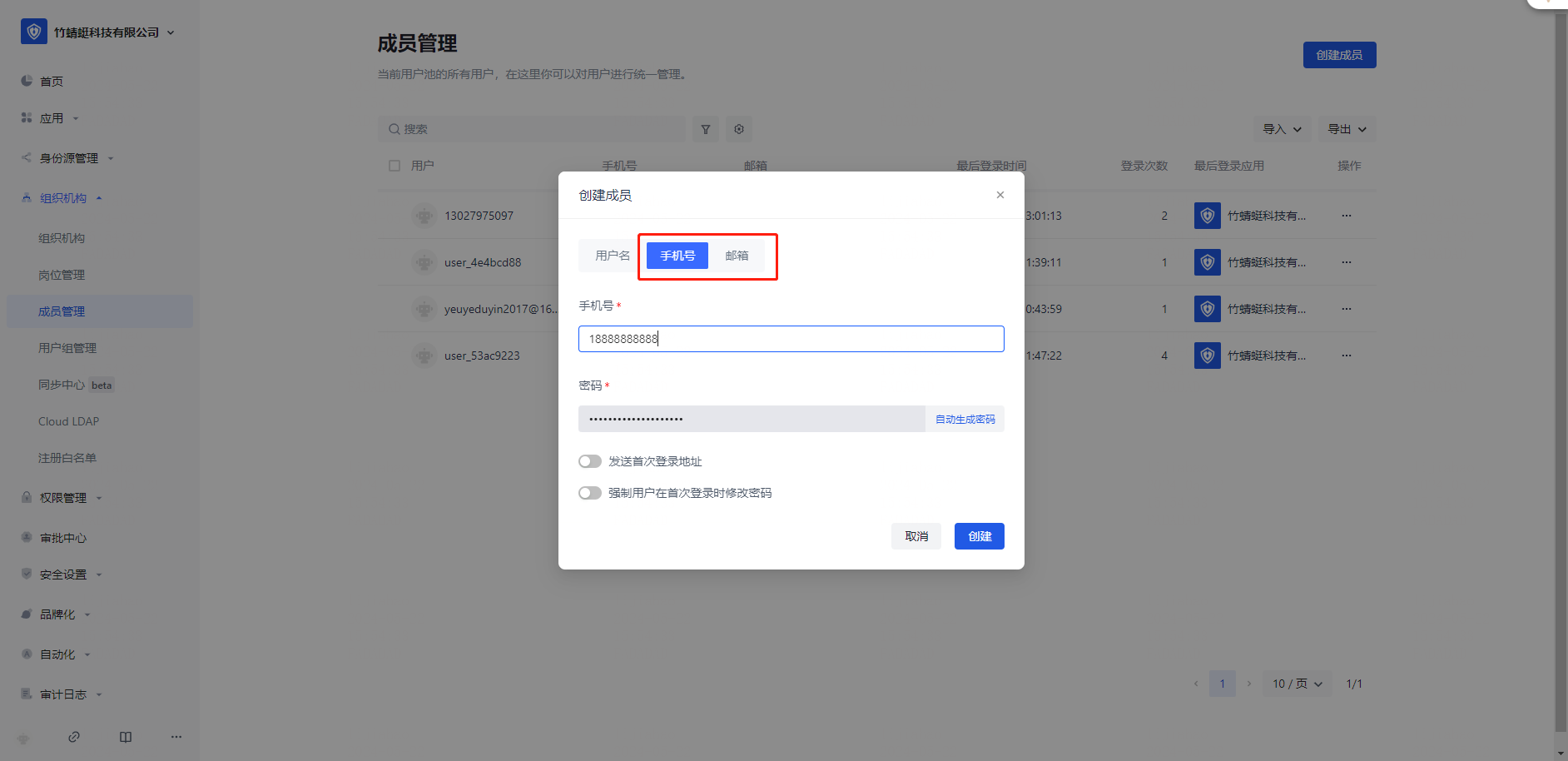
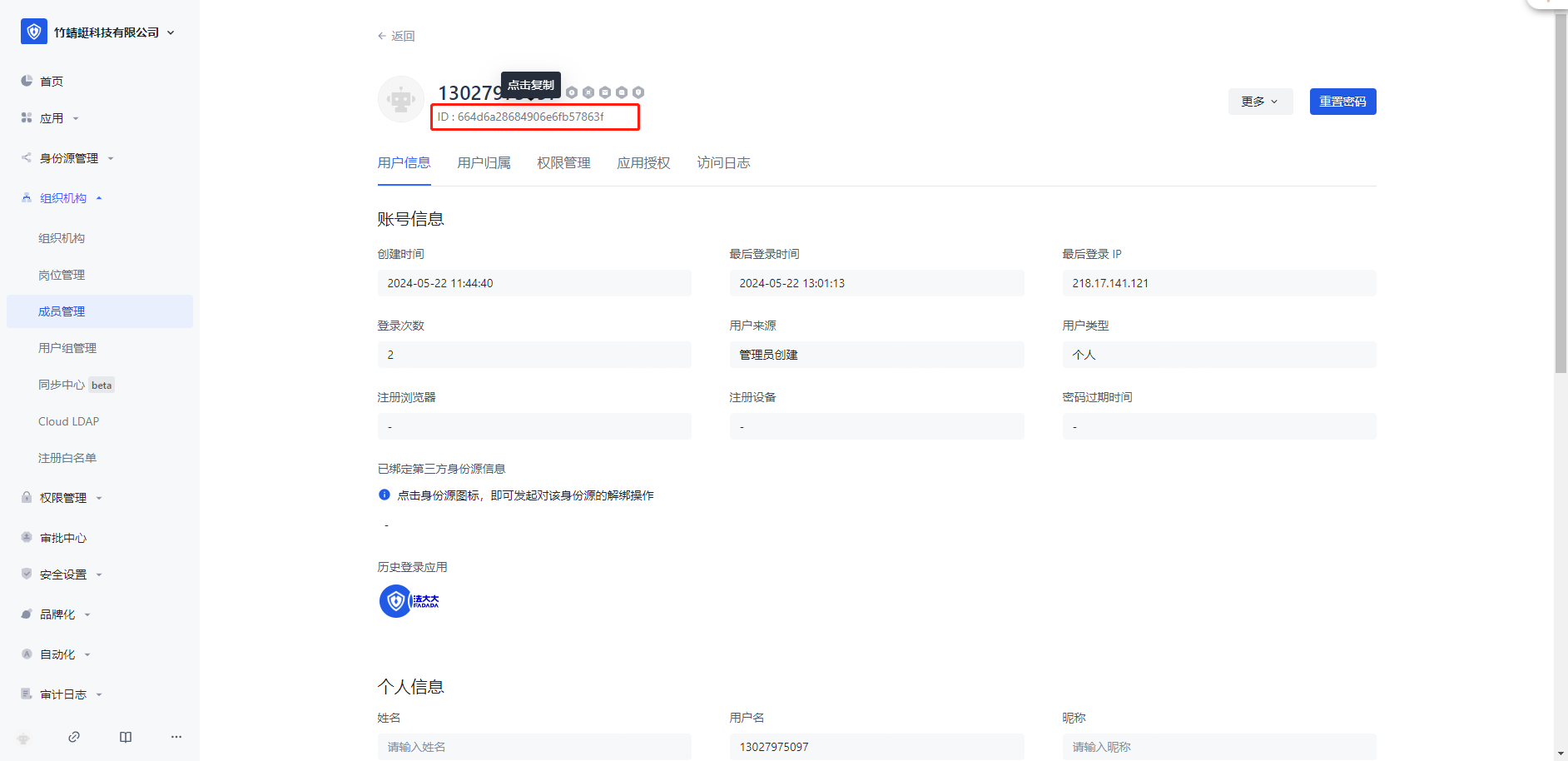
Note: Configure the user to be assigned to the application, and record the [user principal name] This name needs to correspond to the [member ID] of the French big enterprise
The configuration is complete on the Microsoft Entra ID.
3. SaaS configuration (it is recommended to open another browser) :
Step 1. Configure single sign-on
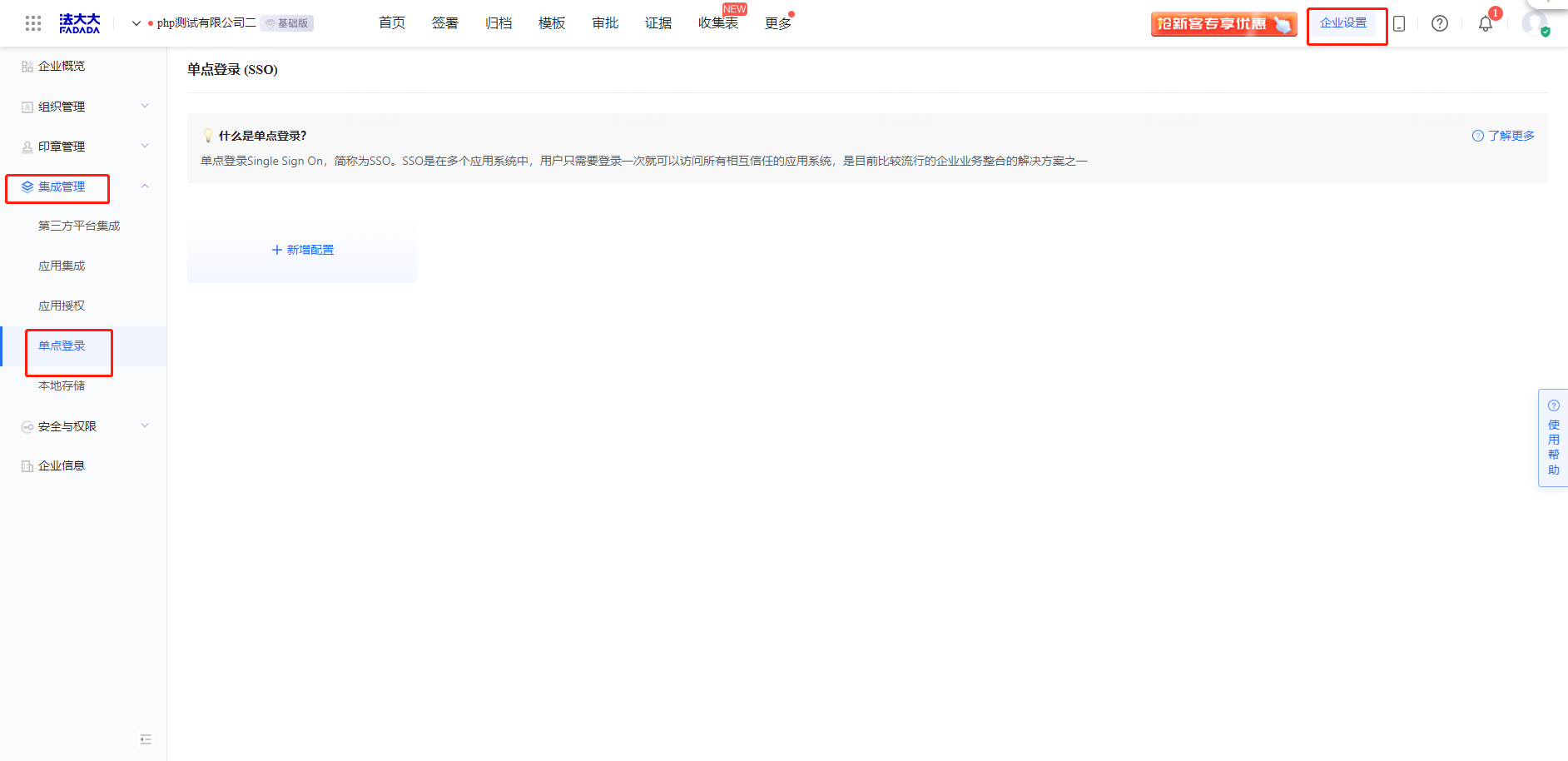
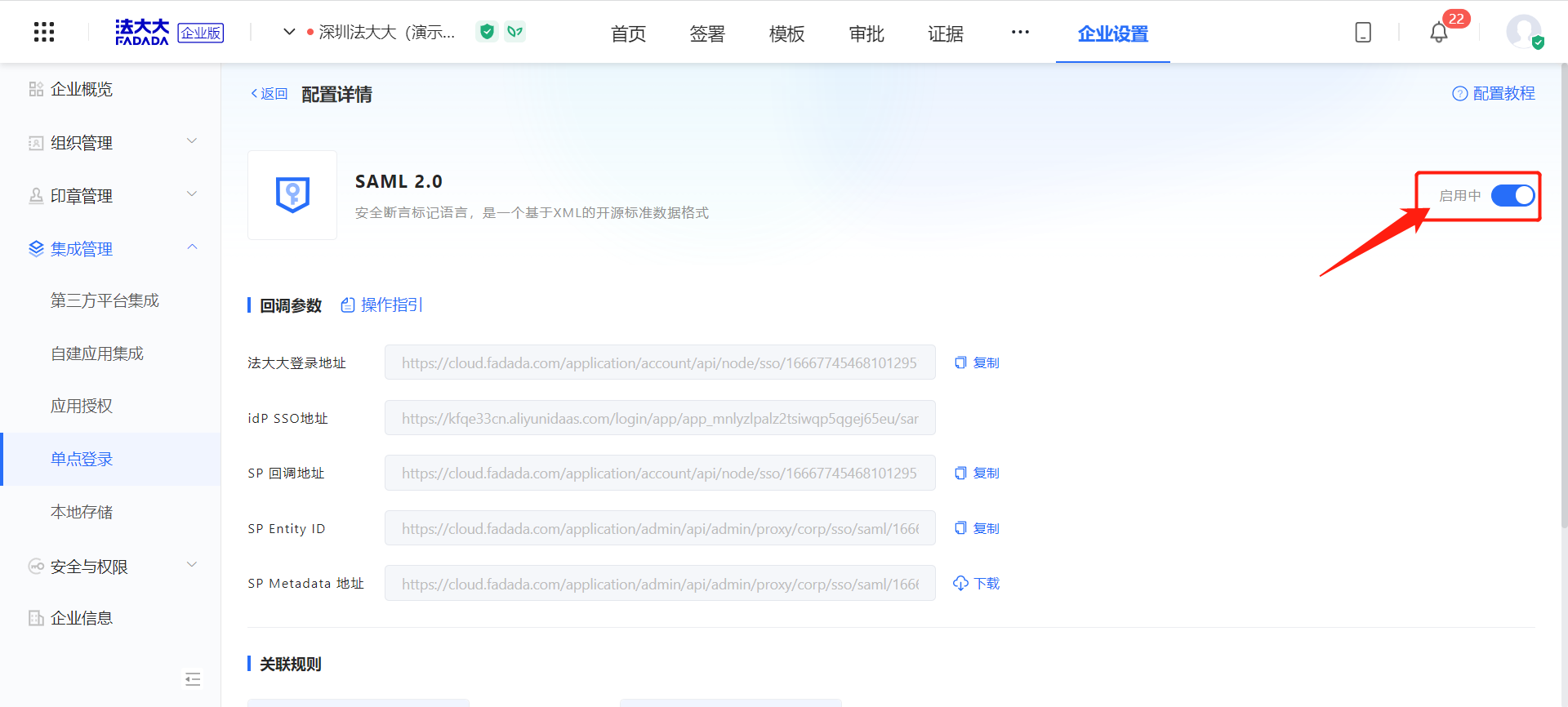
Operation 1: Log in to Fada SaaS Platform (Fada SaaS Service Platform) and enter the 【 Enterprise Settings 】-【 Integrated Management 】-【 Single sign-on 】 page
Operation 2: Click [Add Configuration] to enter the configuration page
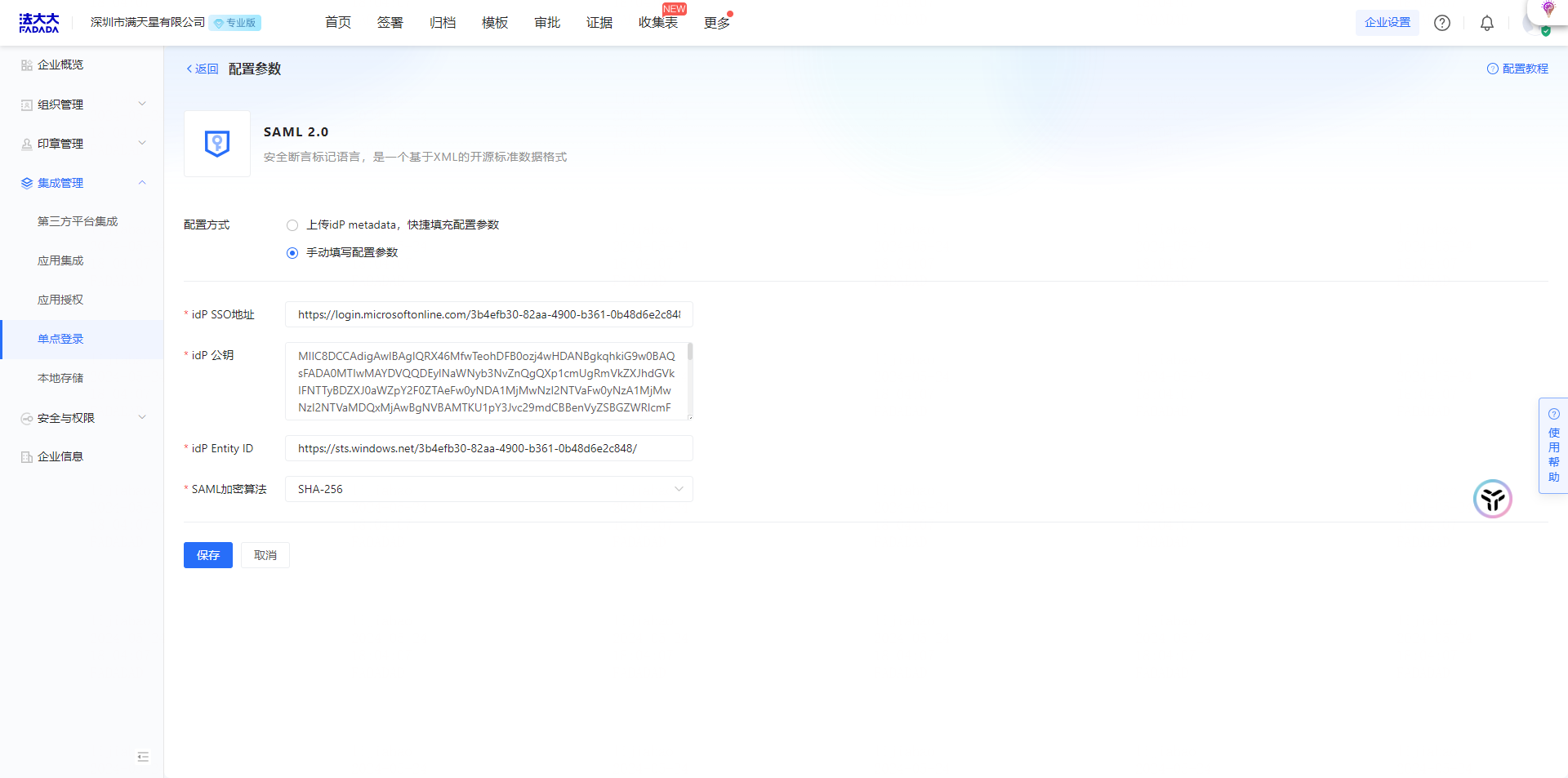
Note: Only one single sign-on configuration can be configured for an enterprise account.
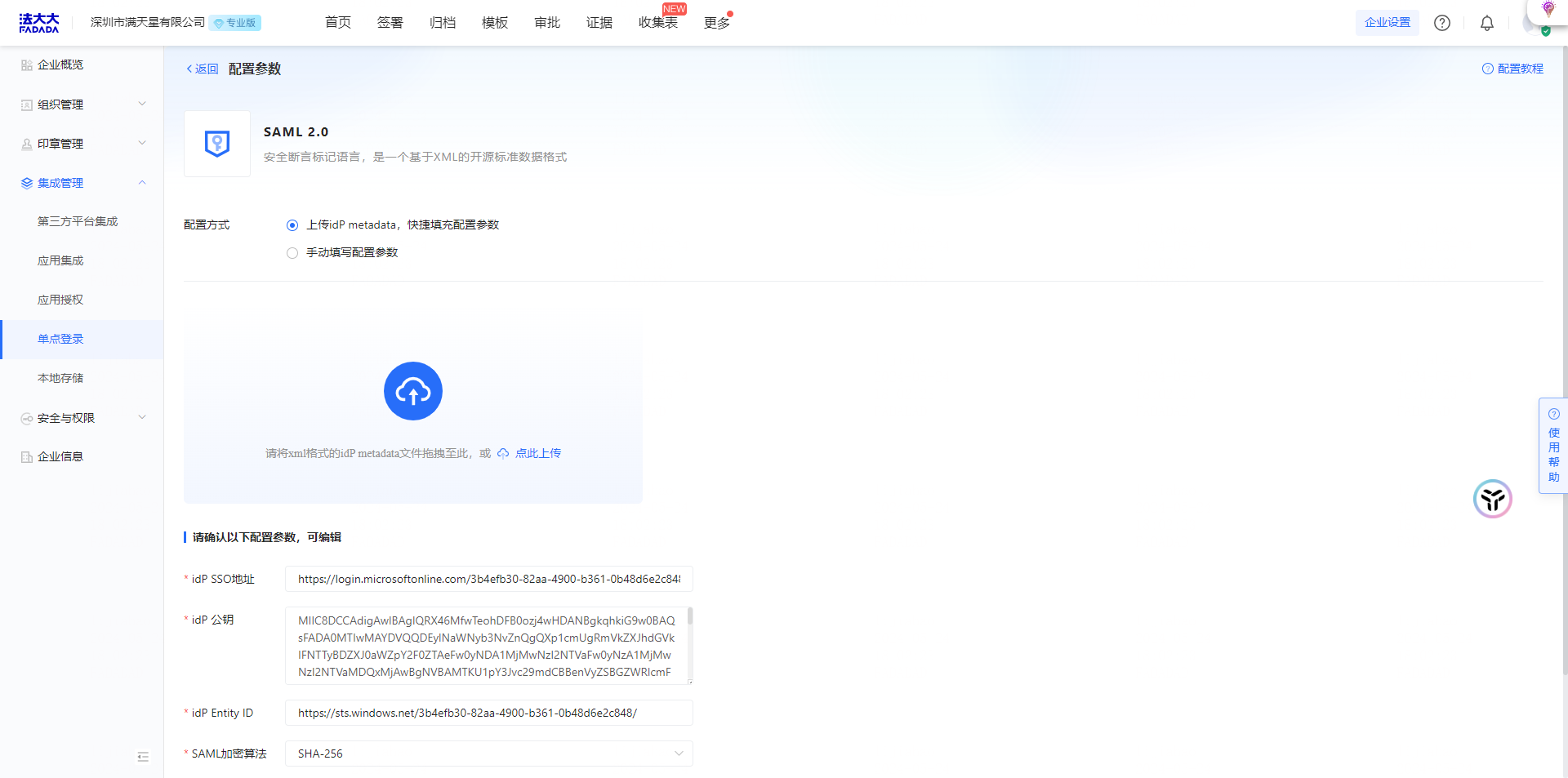
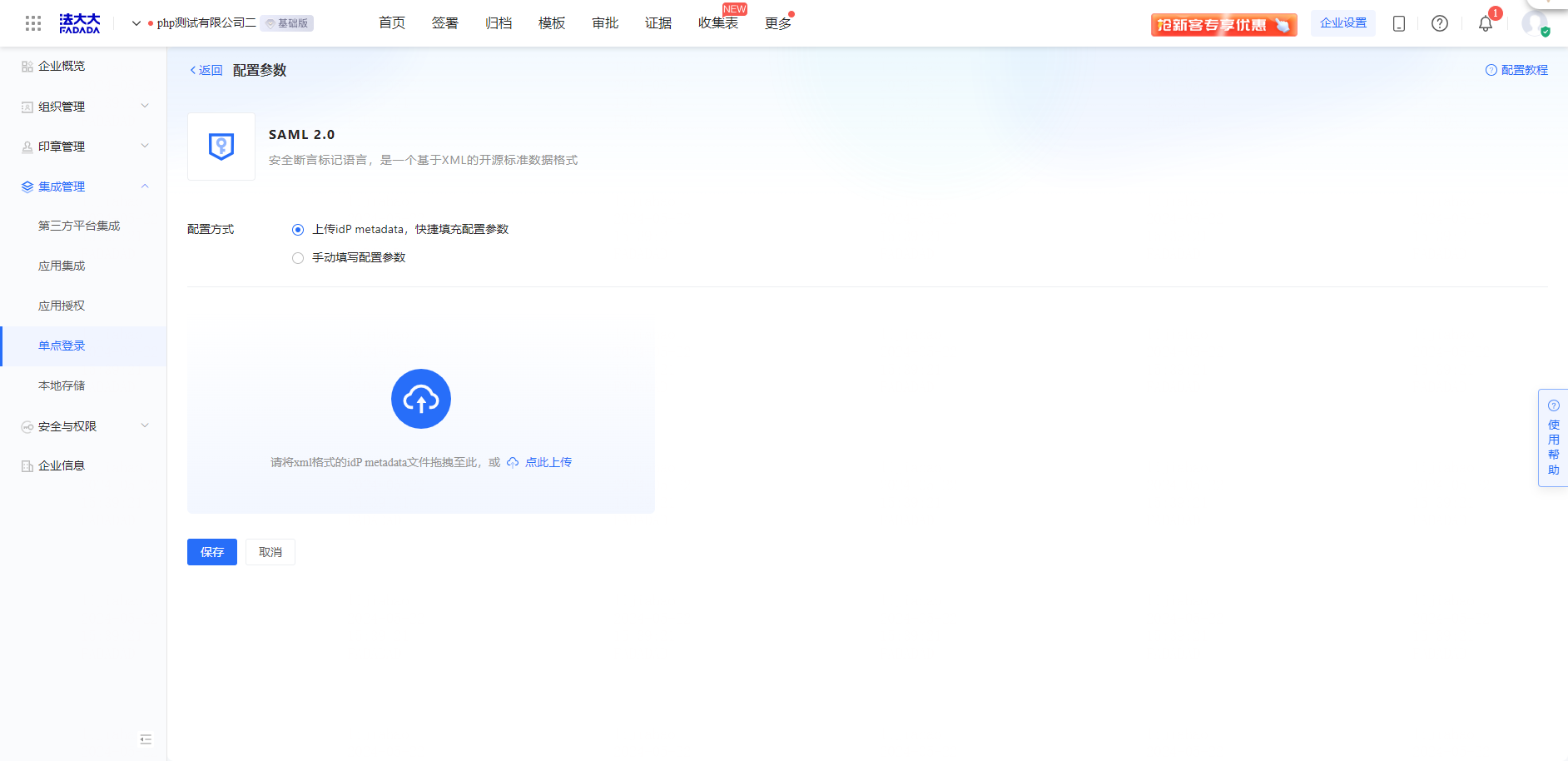
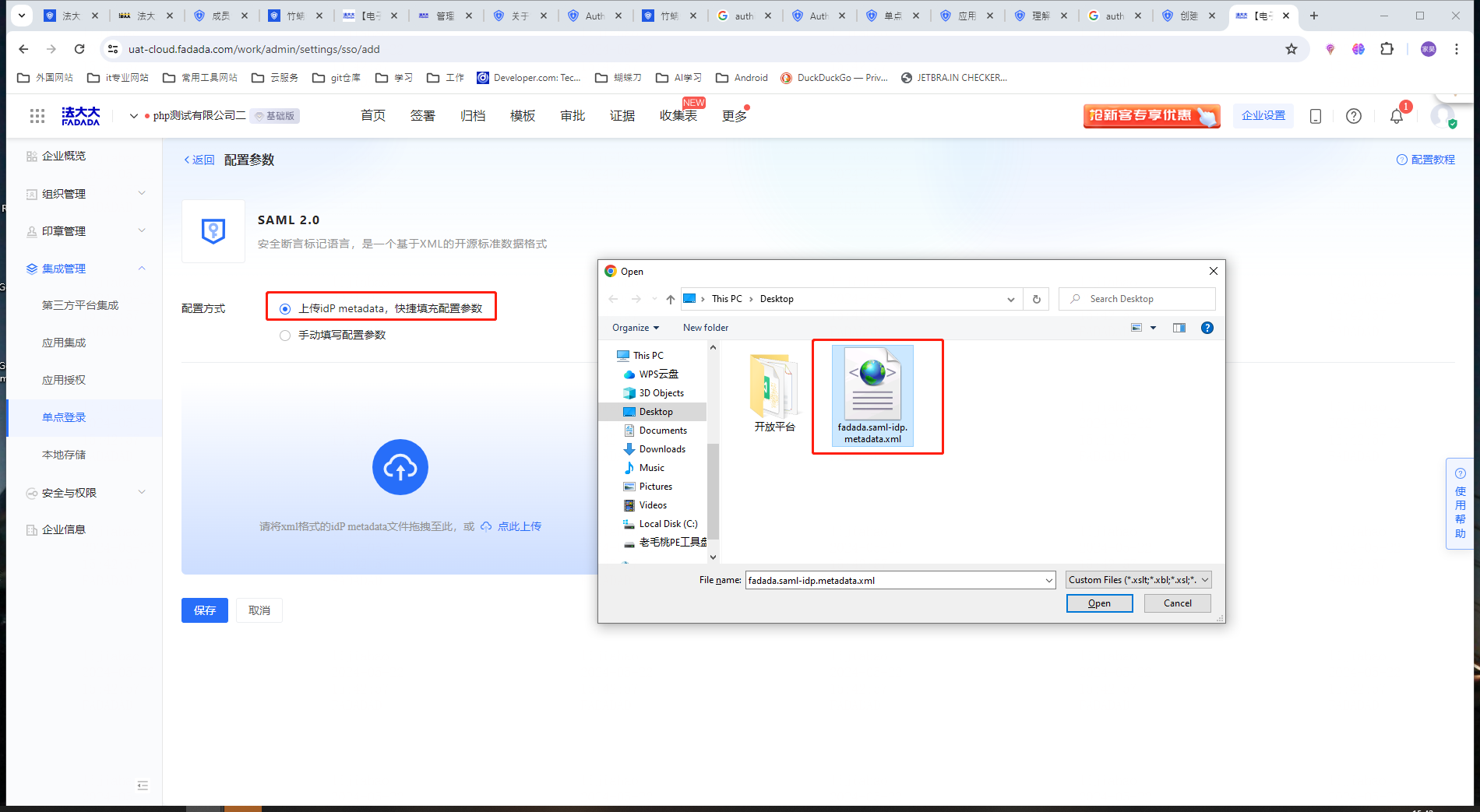
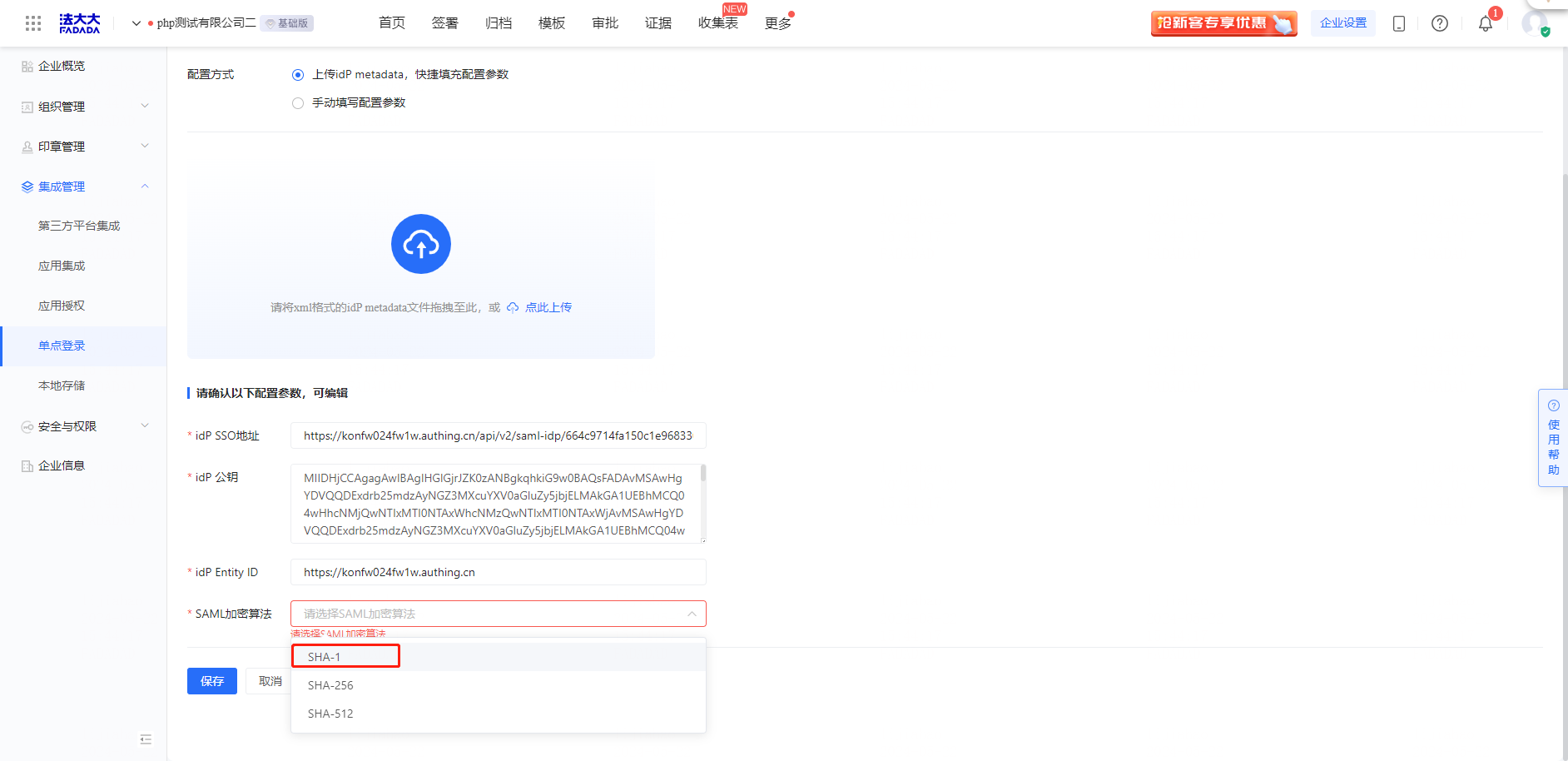
Operation 3: Upload the IdP metadata file to quickly fill in the configuration parameters
Note: It is the.xml file of Shenzhen Mantistar Co., Ltd. downloaded during the configuration of Microsoft Entra ID terminal
Operation 4: Select the encryption algorithm SHA-256 and save the configuration
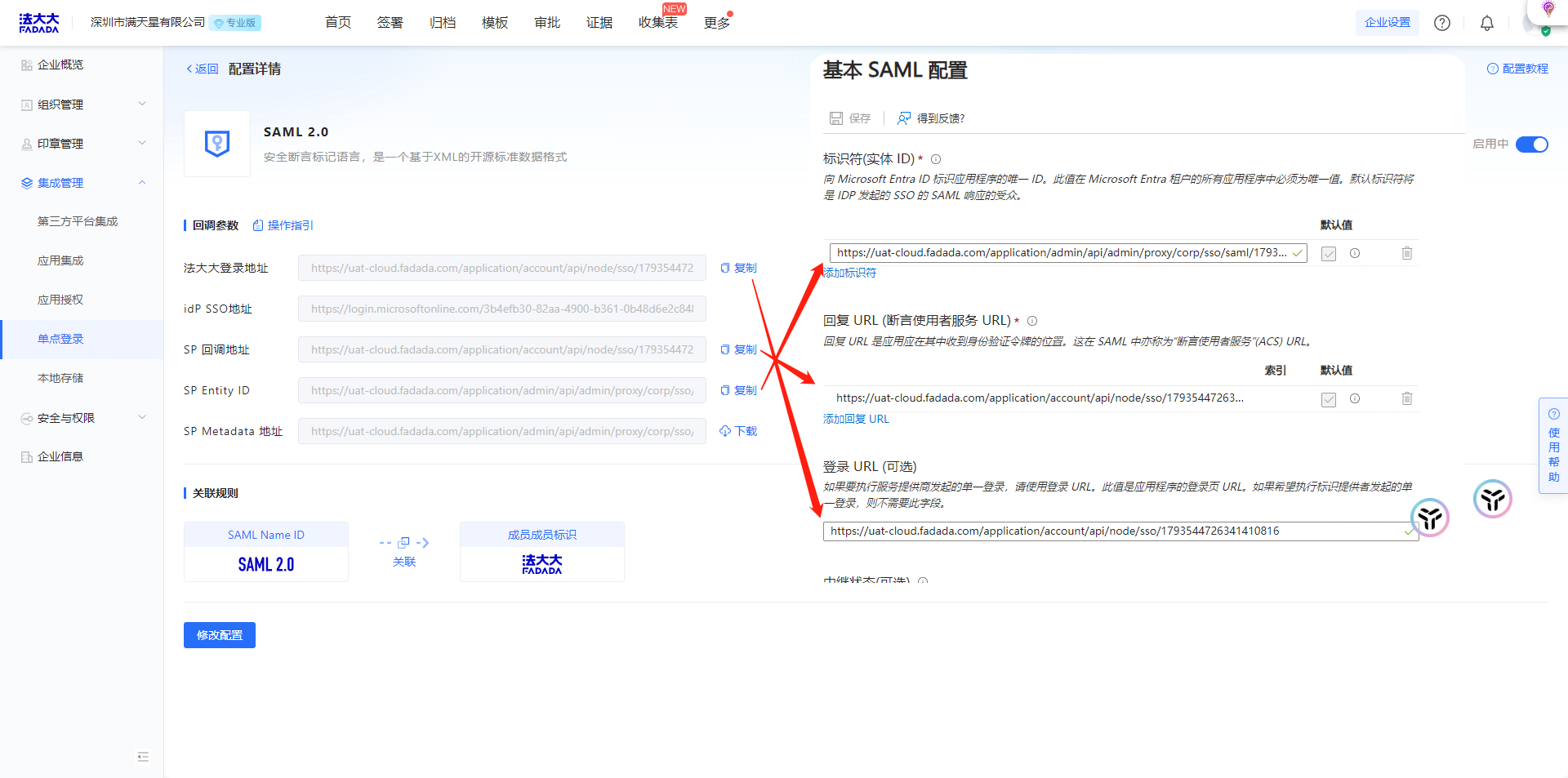
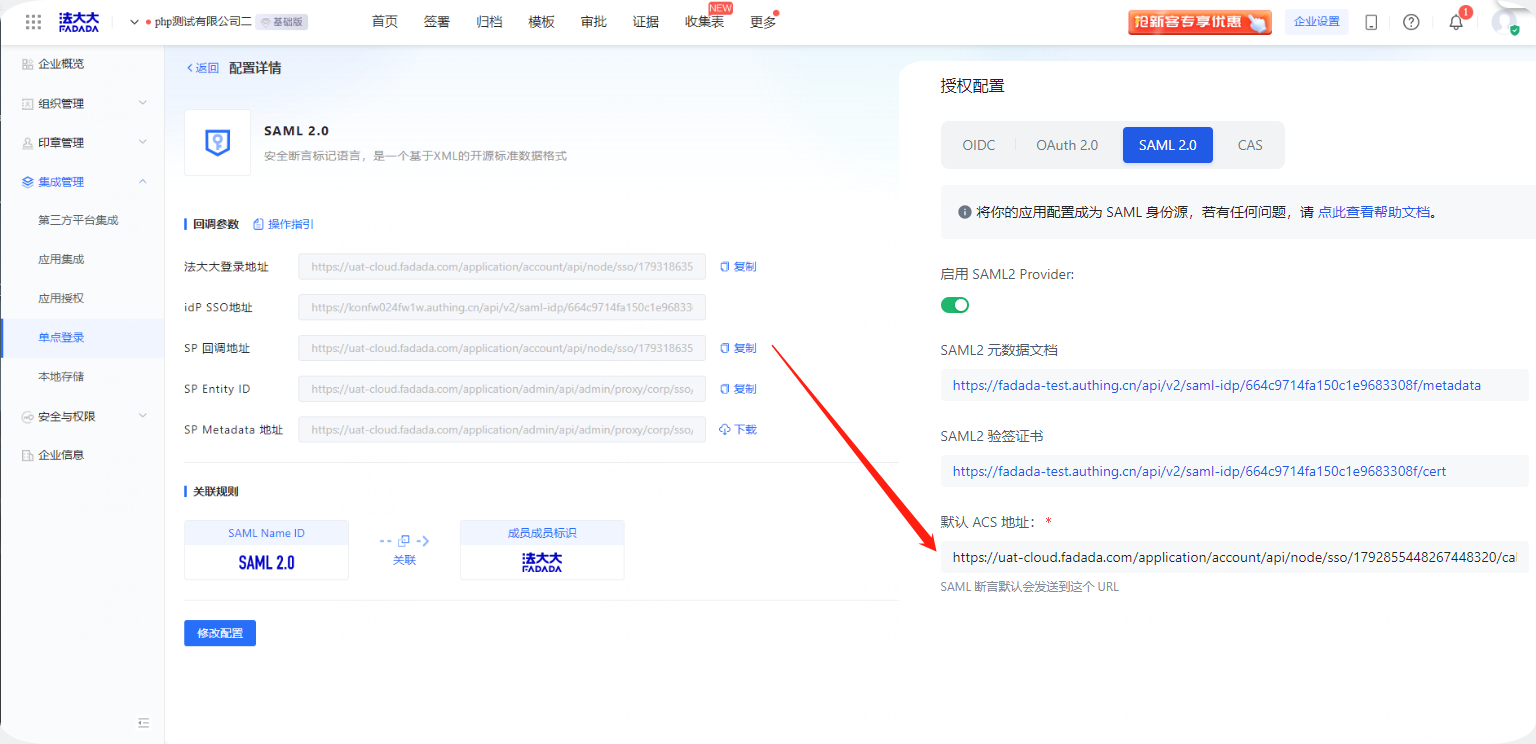
Action 5: Copy the SP callback address and paste it to the identifier (entity ID) and reply URL (assert user service URL) in the basic SAML configuration on the Microsoft Entra ID.
Note: Download the federation metadata again after modifying the parameters on the Microsoft Entra ID side. XML to the local computer, re-upload once to method big SSO refresh replace the previous configuration parameters.
Action 6: Enable single sign-on SAML2.0 configuration
To this method greatly SaaS side configuration is completed.
4. The Microsoft Entra ID Single login user account is associated with the FADA SaaS user account
Account association rules:
Users of the Microsoft Entra ID side application:
Follow the previous steps to record the user principal name assigned to the application
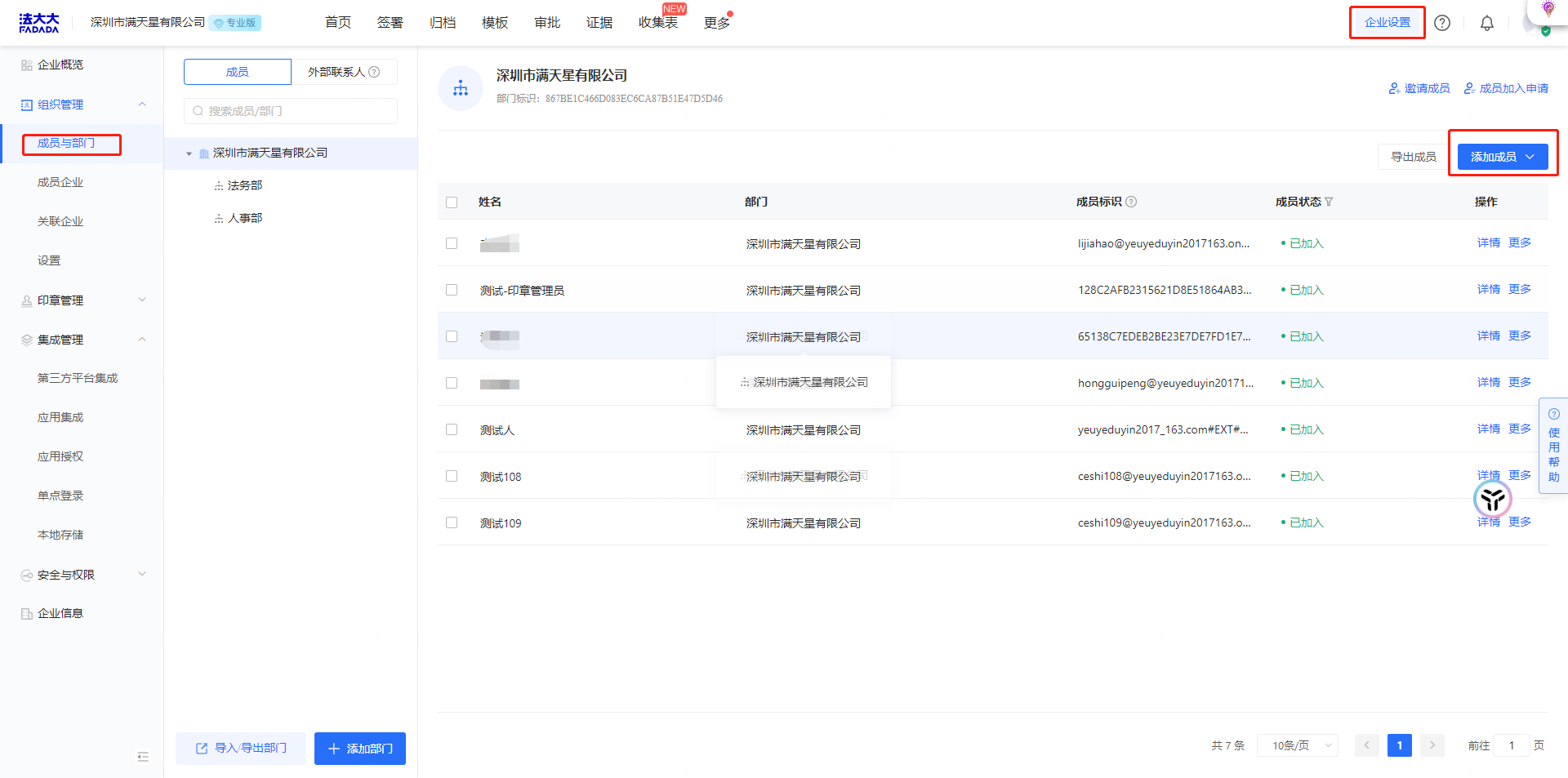
Fada SaaS terminal corresponding to the new user account:
The steps are as follows:
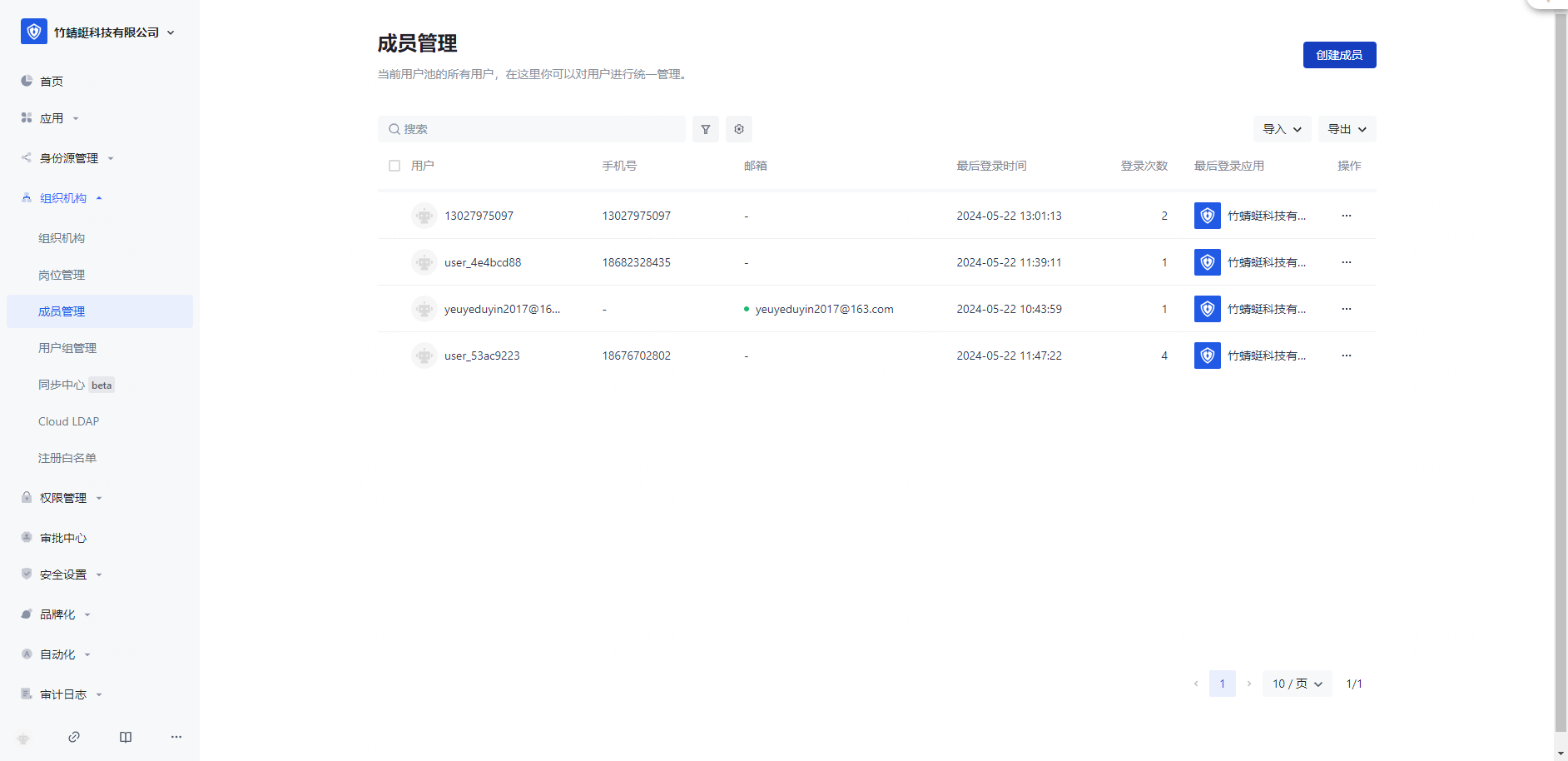
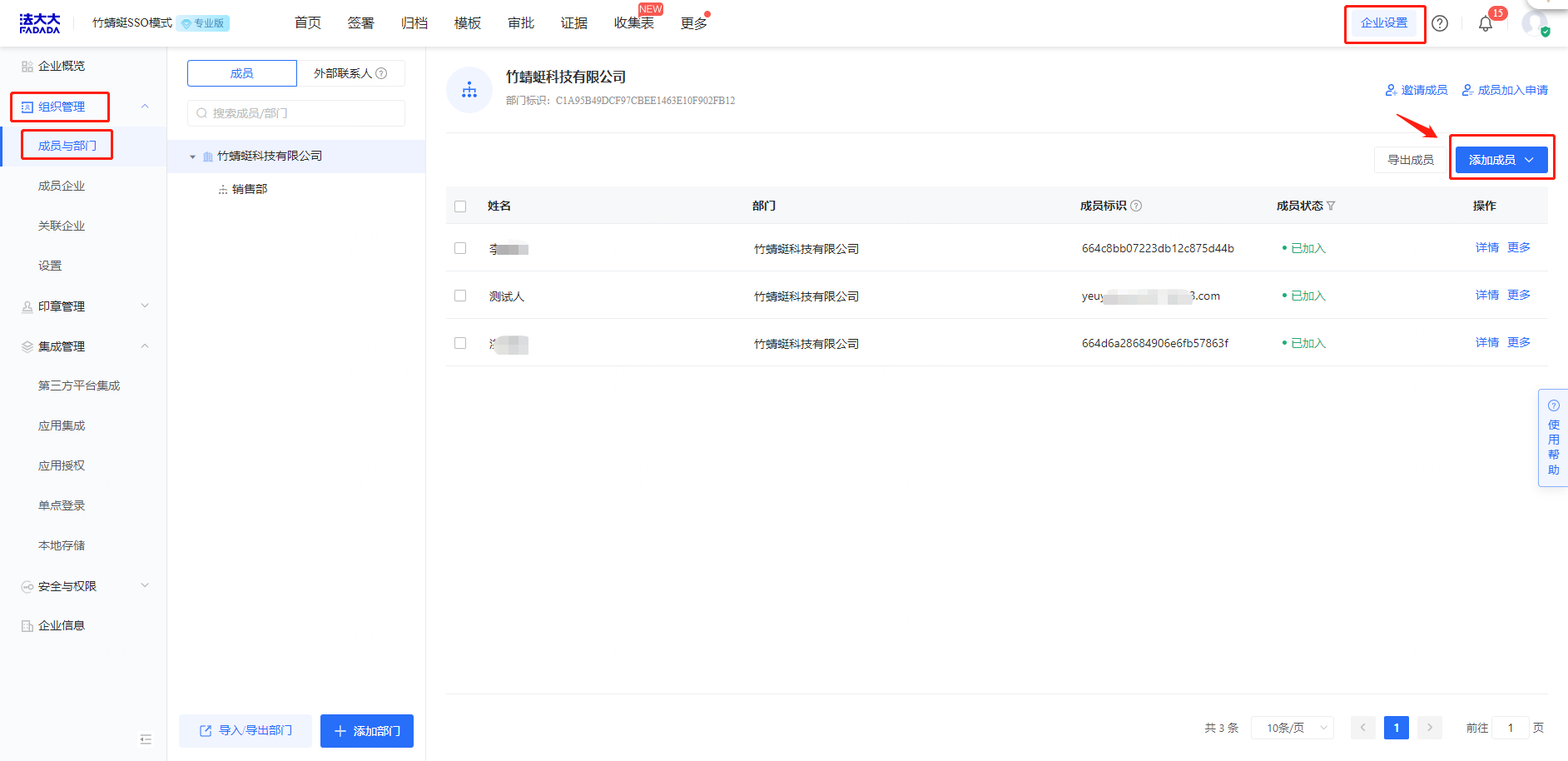
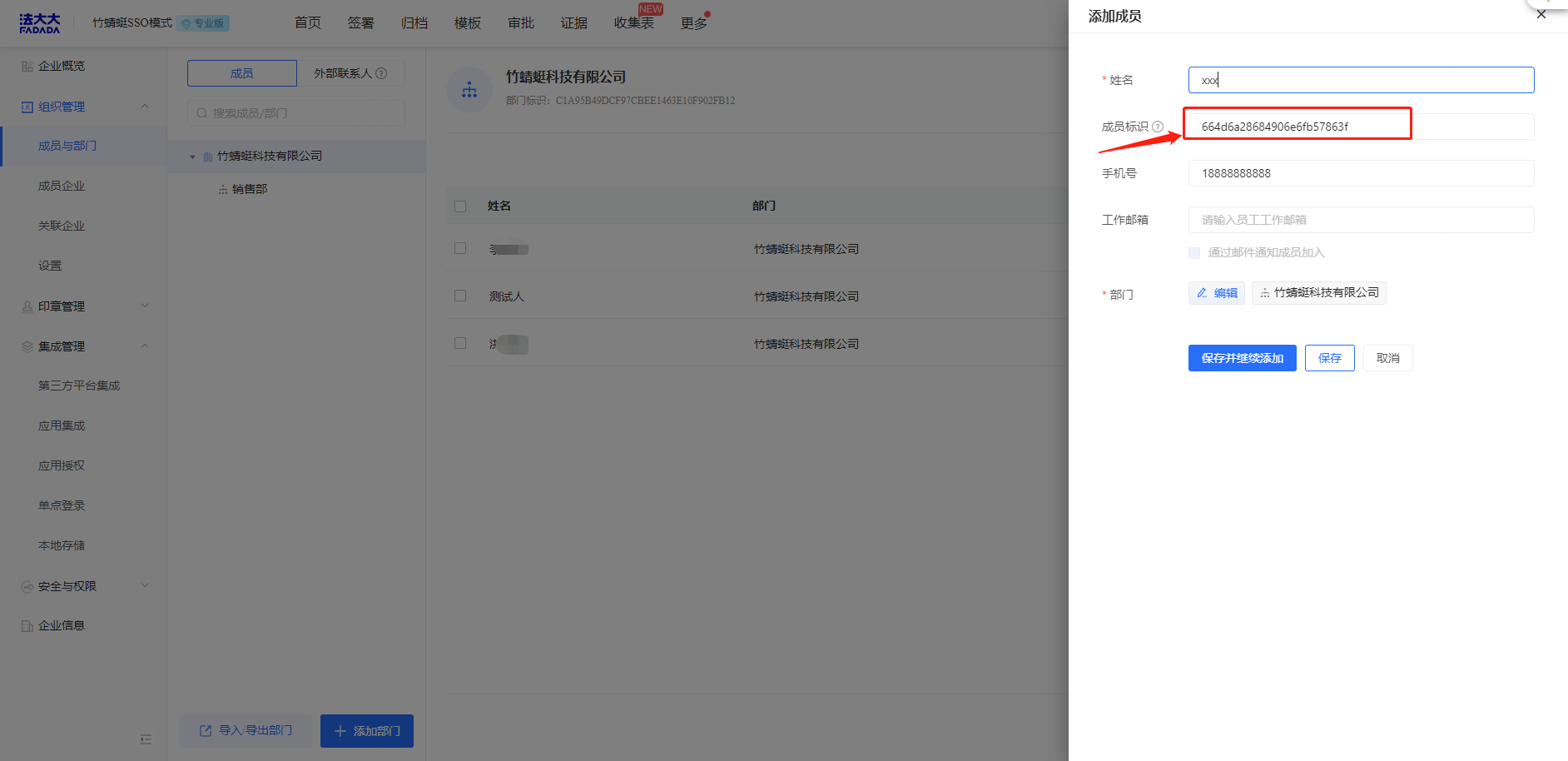
Add enterprise members manually or in batches
Copy [User Principal Name] of the Microsoft Entra ID to [Member ID] and save. The two accounts are associated and SSO can be performed.
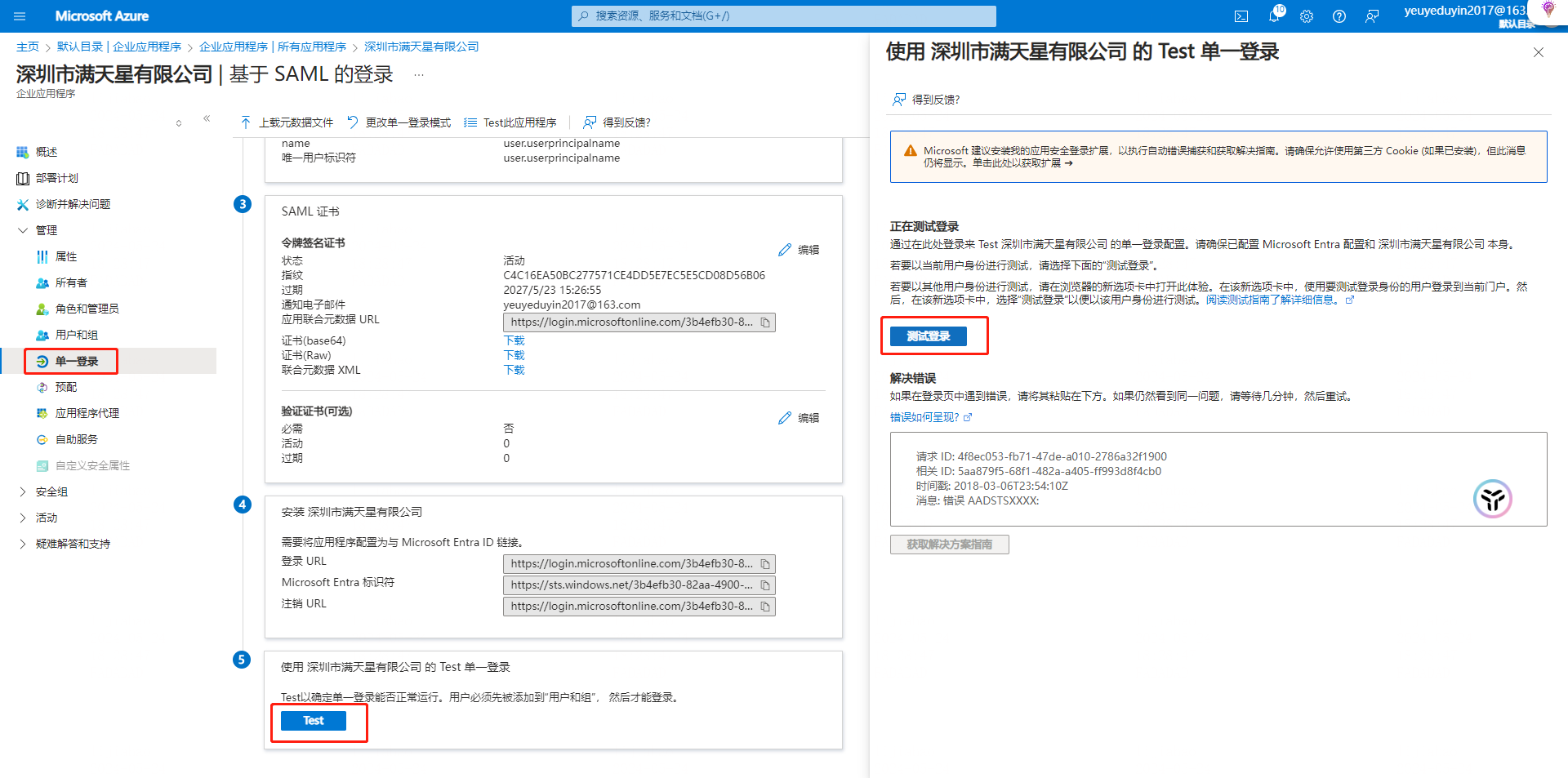
5. Single sign-on test
Access [Enterprise Application] - [New Application] - [Single Sign-on] with Microsoft Entra ID
2. Example of Authing operation configuration
1. Use Authing to implement SSO
Authing: Provides professional identity authentication and authorization services for enterprises and developers on the cloud
Product address: Single sign-on SSO - Pre-integrated 2000+ application, fast implementation of secure unified identity authentication | Authing
Users can use Authing to achieve unified account login, and Azure Active Directory, Microsoft Entra ID, Alibaba Cloud IDaaS, and Tencent Cloud Account Connector all provide similar capabilities. The following is a detailed explanation of how to greatly SaaS through Authing Unified login Law.
2. Authing configuration:
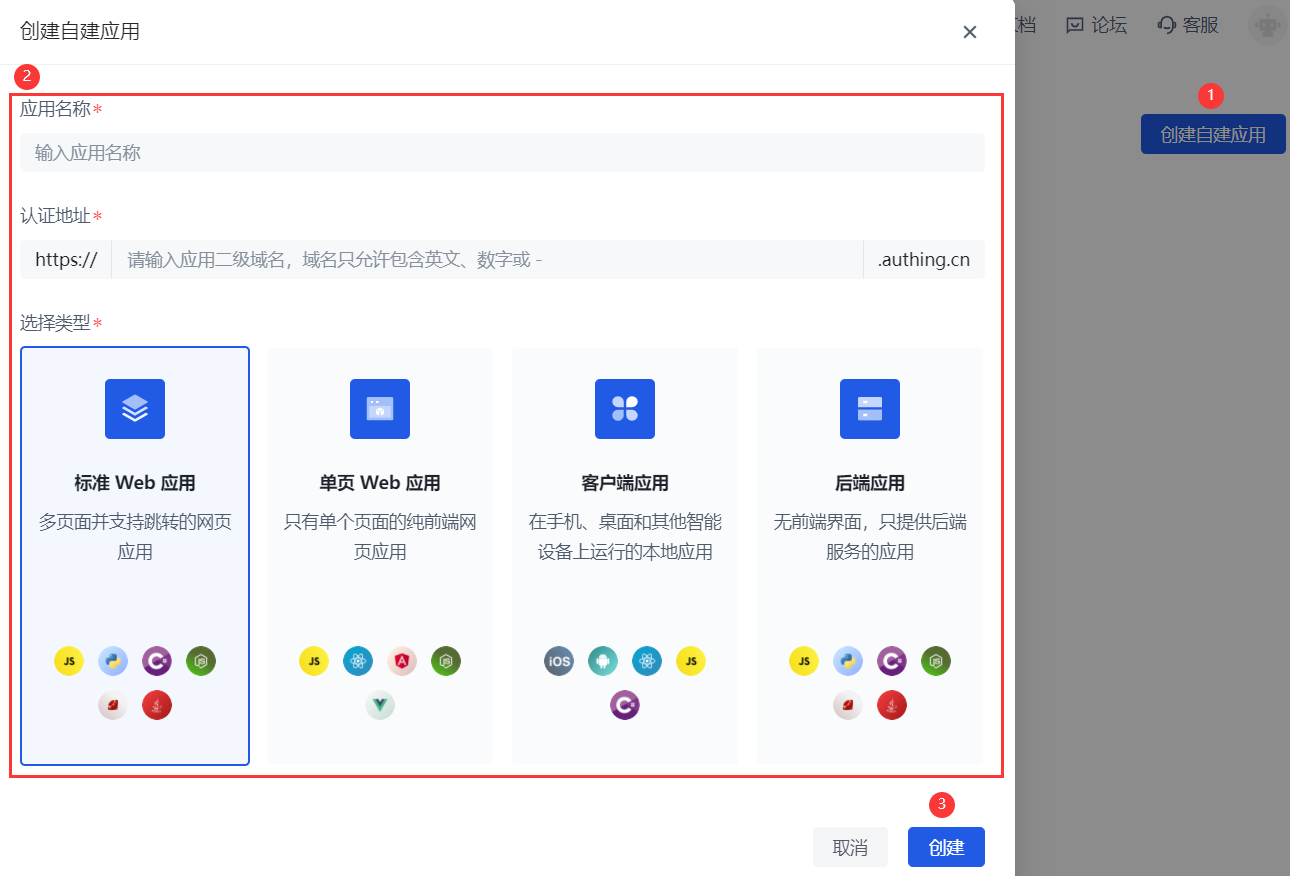
Step 1: Create a self-built application
Operation: Go to 【 Application 】-【 Self-built Application 】 Click 【 Create Self-built application 】
Note: User-defined application name (recommended to be consistent with the enterprise name to be logged in for easy identification), user-defined authentication address (recommended to be consistent with the domain name of the service provider to be logged in for easy identification), select a standard Web application
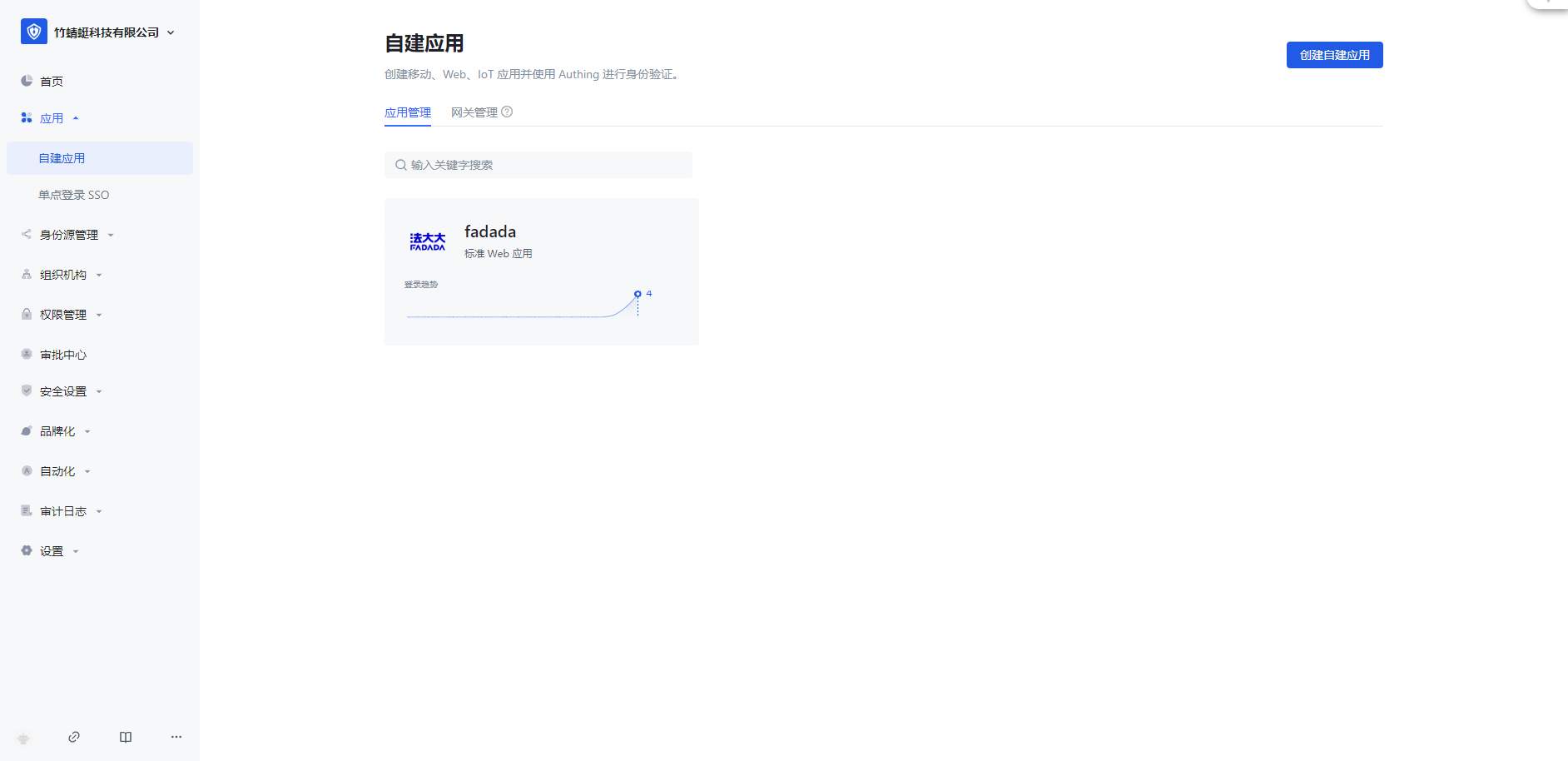
After creation, display as shown in the following figure
Step 2 Configure the self-built application
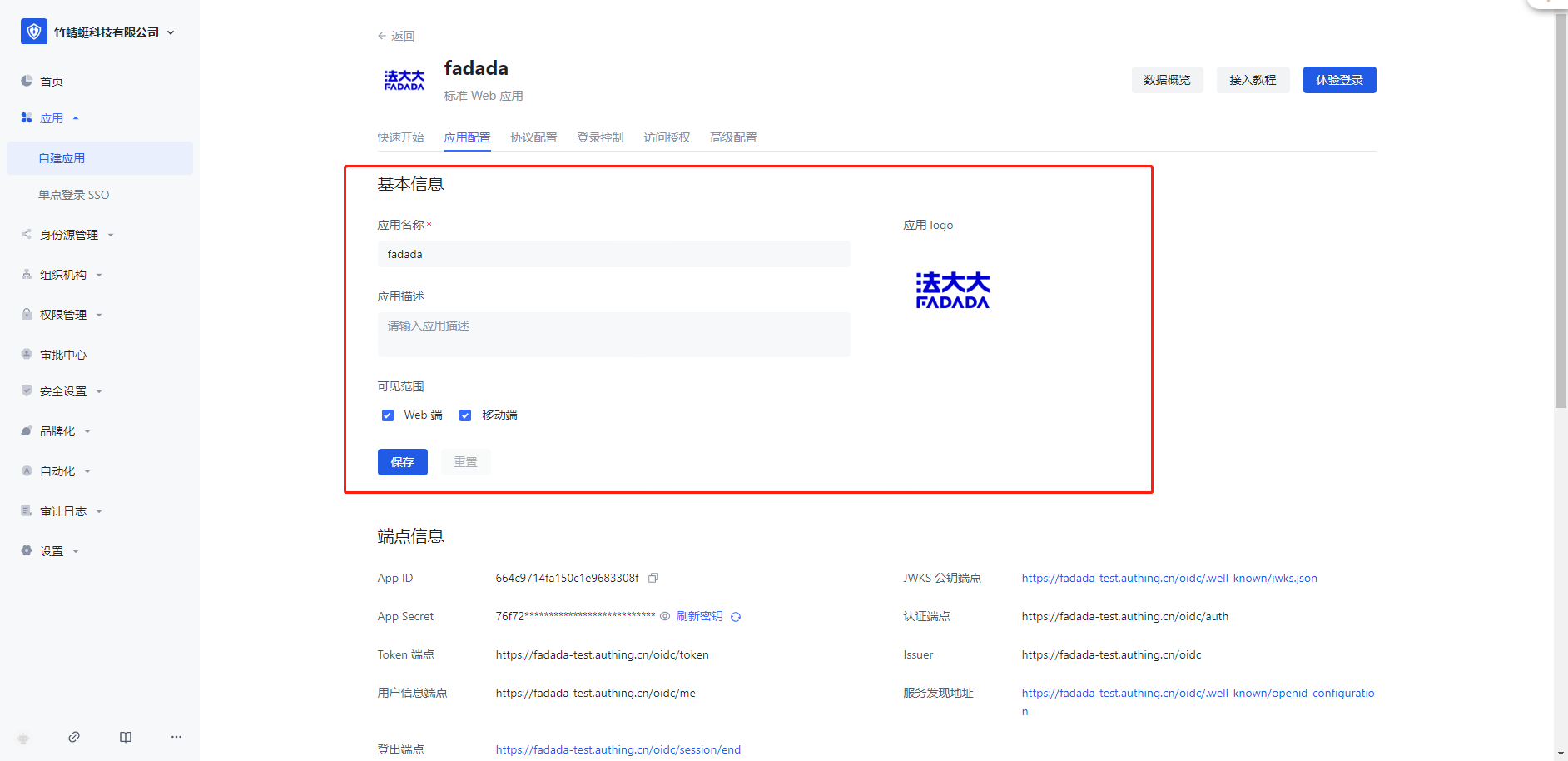
Action 1: Click on the application card to enter [Application Configuration]
Note: The basic application information can be maintained, and other information can be kept by default
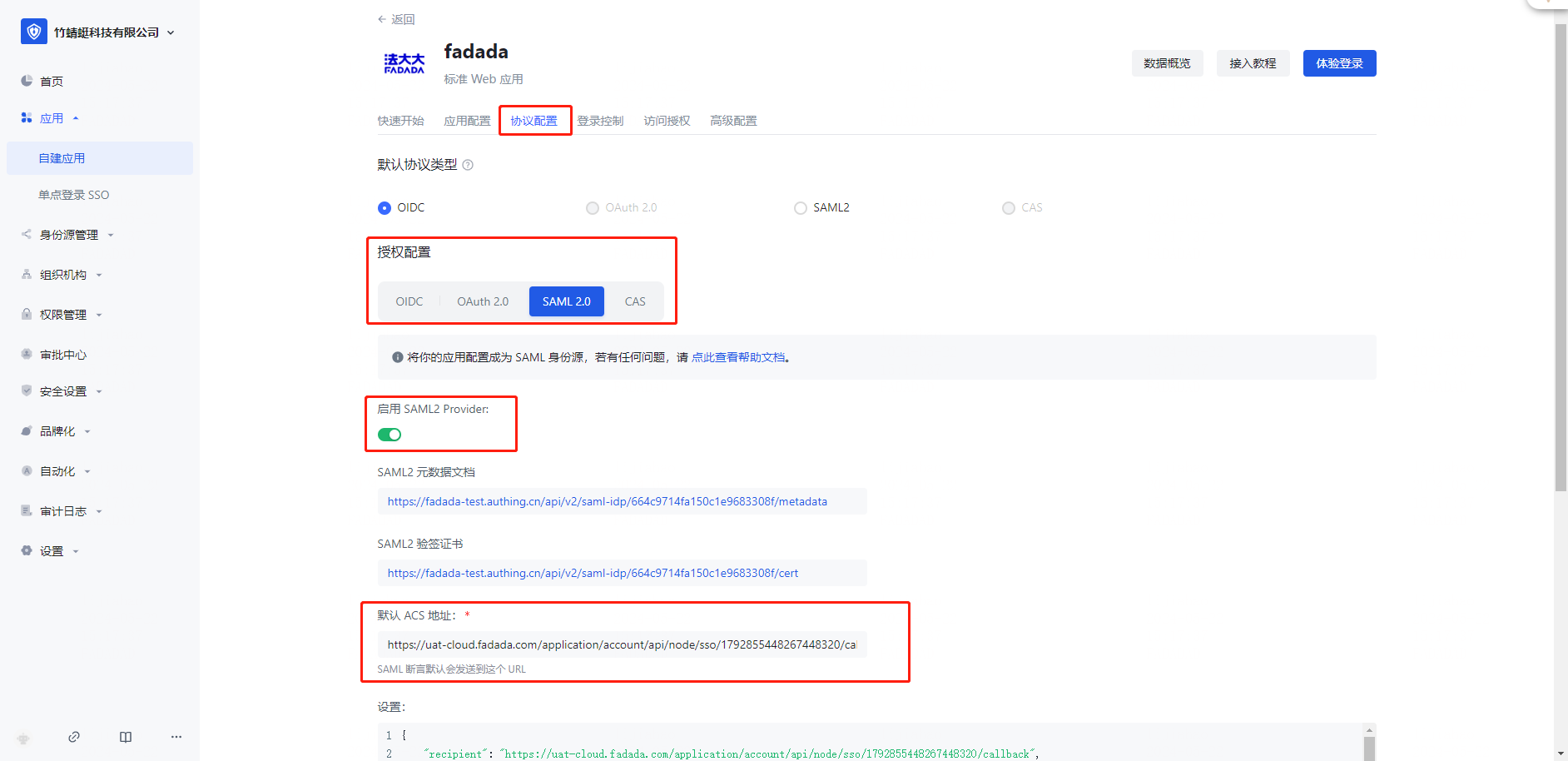
Operation 2: Switch to the [Protocol Configuration] page, select Authorization configuration [SAML 2.0], and click Enable SAML2 Provider
Note: The current default protocol is OIDC. To disable other protocols, you need to enable and save the Settings in Authorization Configuration.
Note: When saving for the first time, the default ACS address is mandatory. You can enter an address at will.
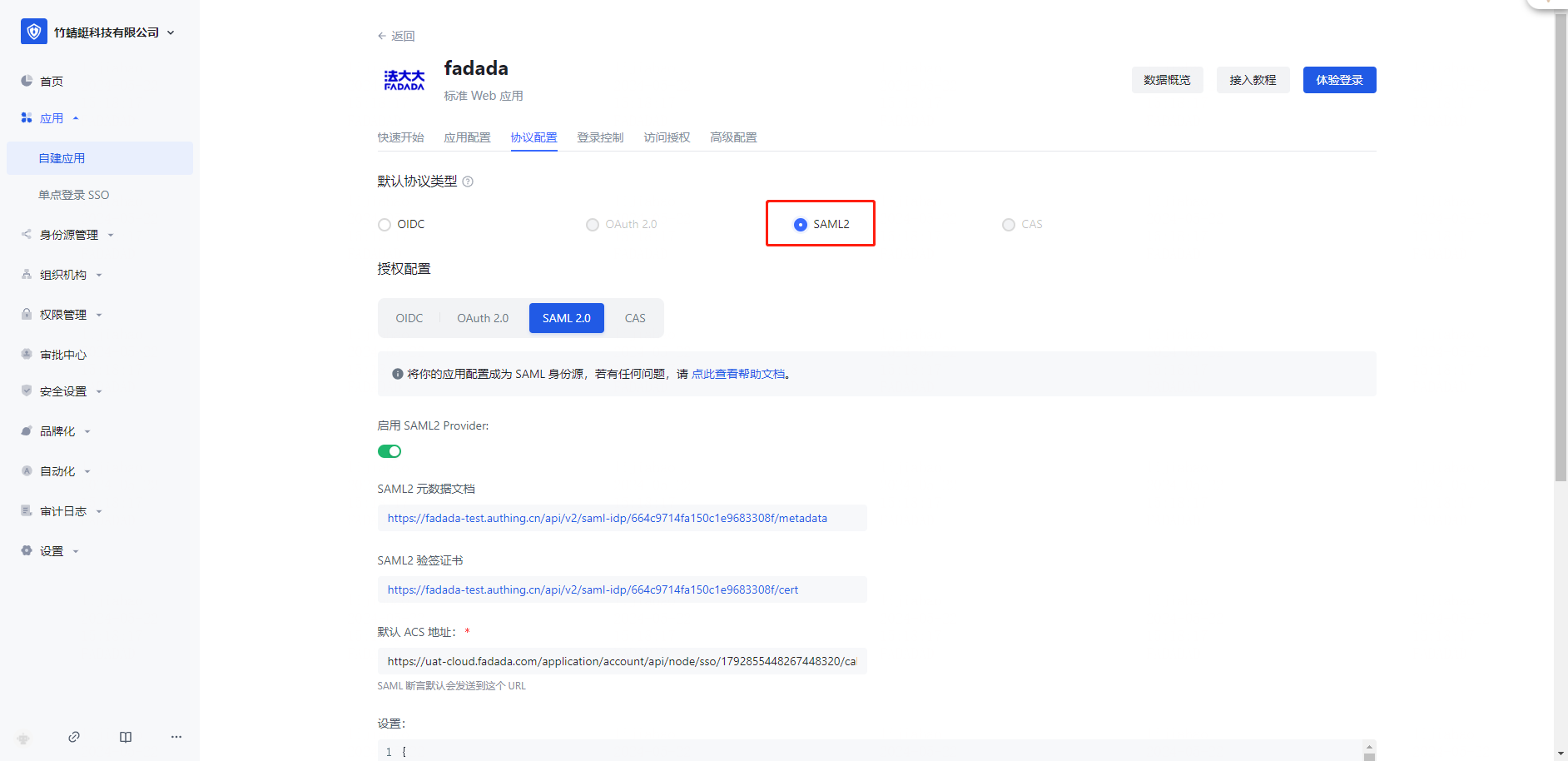
Action 3: Click Save to change the default protocol type [SAML2].
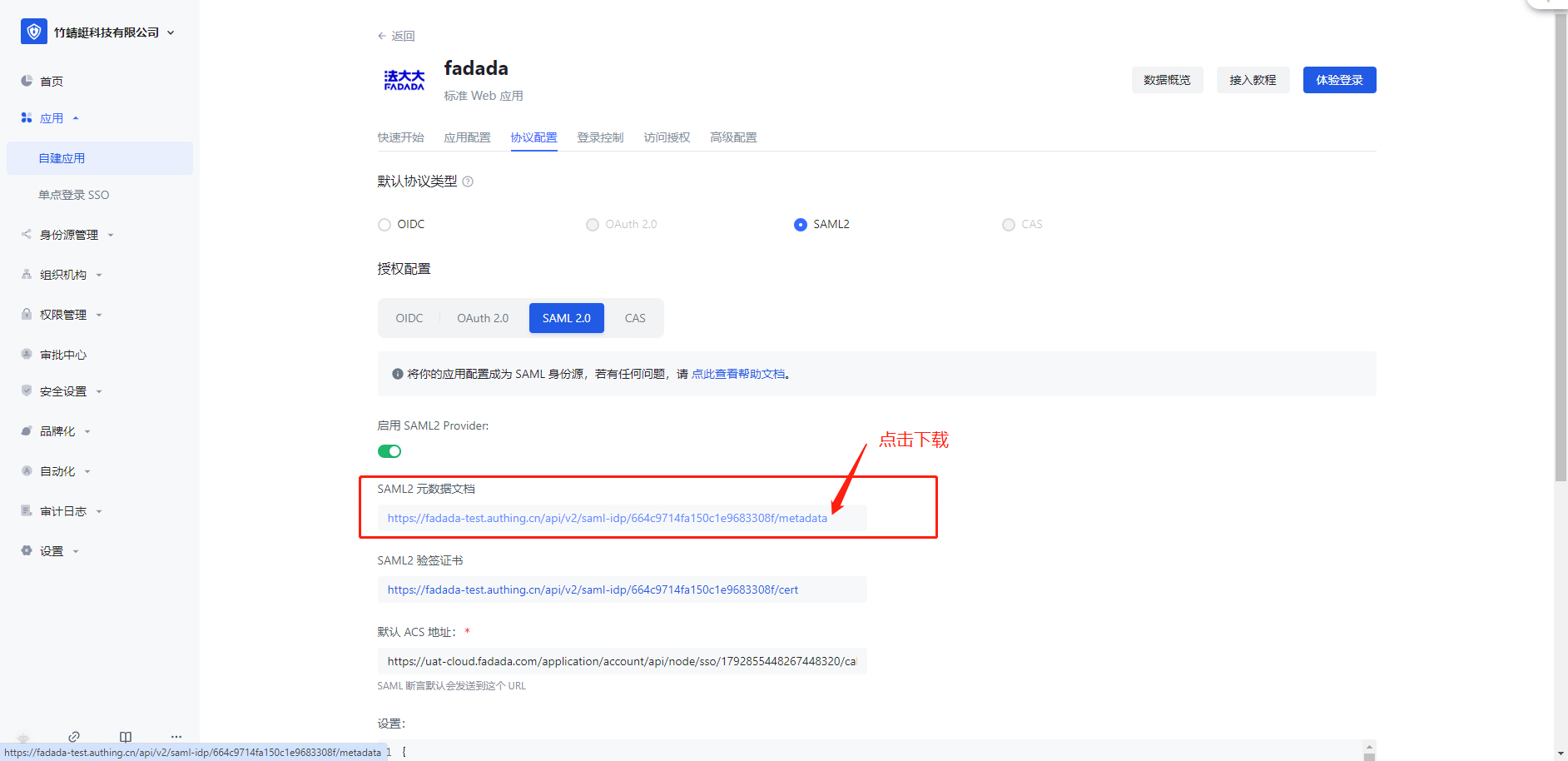
Operation 4: Download the SAML2 metadata document to the local PC
Operation 5: Switch to the [Login Control] page and configure the login mode
Note: Select as required
Operation 6: Switch to the Access Authorization page and configure the access permission of the Authing login account to the application
You can configure permissions according to multiple dimensions.
Step 3. Configure SSO
Operation 1: Select "Application" - "SSO" from the left menu and select "Application Management"
Action 2: Click [Add Self-built App]
Operation 3: Switch the Configuration page
Note: Configure basic information and general login information, as required, or the default value
The configuration of Authing is complete.
3. SaaS configuration (it is recommended to open another browser) :
Step 1. Configure single sign-on
Operation 1: Log in to Fada SaaS Platform (Fada SaaS Service Platform) and enter the 【 Enterprise Settings 】-【 Integrated Management 】-【 Single sign-on 】 page
Operation 2: Click [Add Configuration] to enter the configuration page
Note: Only one single sign-on configuration can be configured for an enterprise account.
Operation 3: Upload the IdP metadata file to quickly fill in the configuration parameters
Note: It is the metadata.xml file downloaded during the configuration on the Authing
Operation 4: Select the SHA-1 encryption algorithm and save the configuration
Operation 5: Copy the SP callback address and paste it to Authing [Self-created application] - [Default ACS address]
Action 6: Enable single sign-on SAML2.0 configuration
To this method greatly SaaS side configuration is completed.
4. The Authing unified login system user account is associated with the FADA SaaS user account
Account association rules:
Add a user account on Authing:
The steps are as follows:
You are advised to add the phone number or email address
Go to the user details and copy the user ID (this ID is SAML Name ID)
Fada SaaS added a user account:
The steps are as follows:
Copy the user ID of Authing to [Member ID] and save. The two accounts are associated and SSO can be performed.
5. Single sign-on test
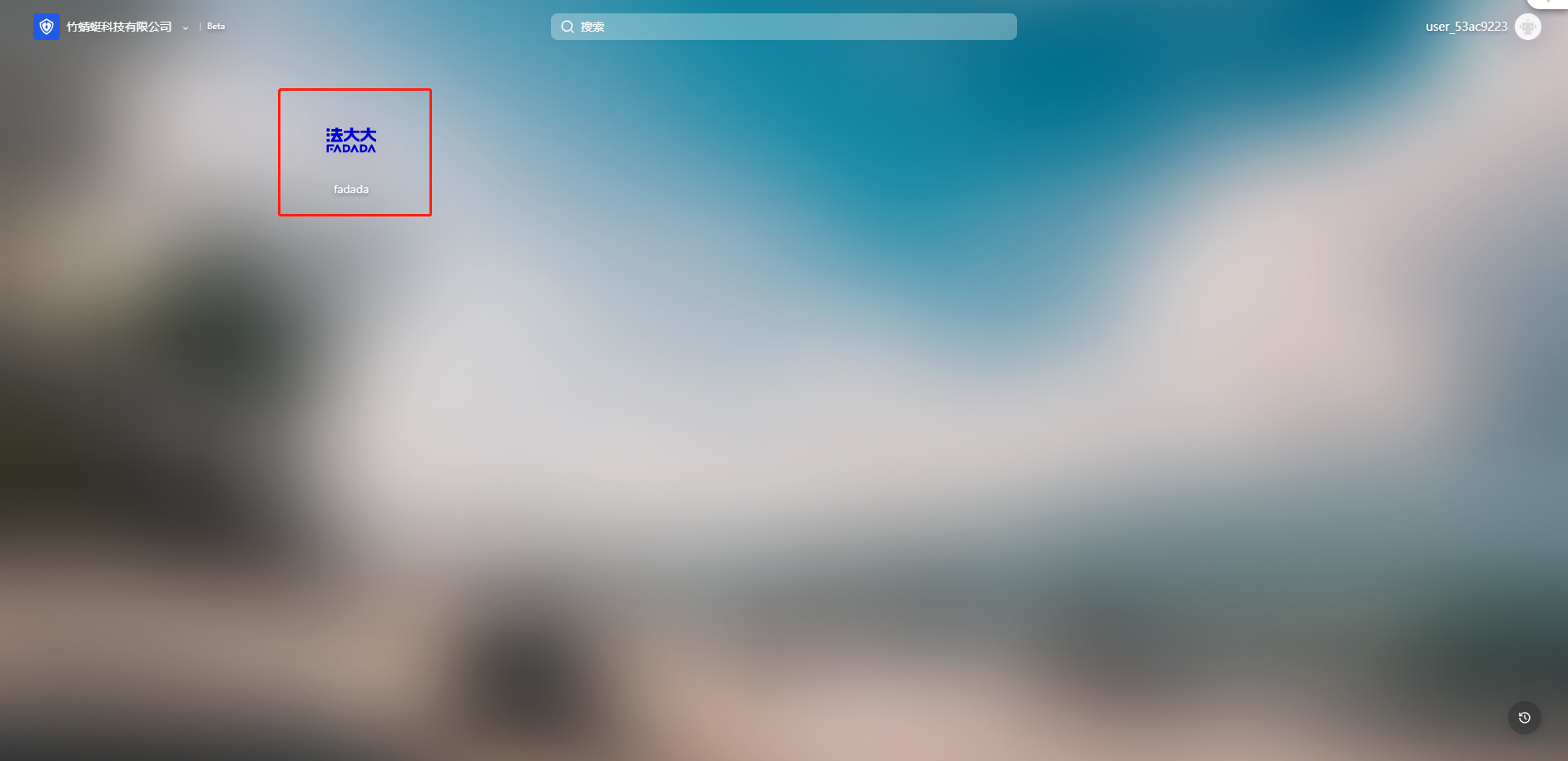
Access the Authing Single Sign-on Application Panel (Unified Login System)
Login page
Click Fada application and log in directly to Fada SaaS platform without logging in again.
Step 1: Access the IdP system and create a new SAML application
Adding SAML Application to IdP "Method Large Enterprise SSO (Example)";
After the SAML application is successfully added, view the application configuration information:
IdP Unique ID (IdP Entity ID) :.. /saml2/meta (Example)
IdP SSO address (IdP Sign-in URL) :.. /saml2/sso (Example)
Public Key Certificate: MIIaux... o2NWV (Example)
Step 2: Access method is large, configure the above SAML application information
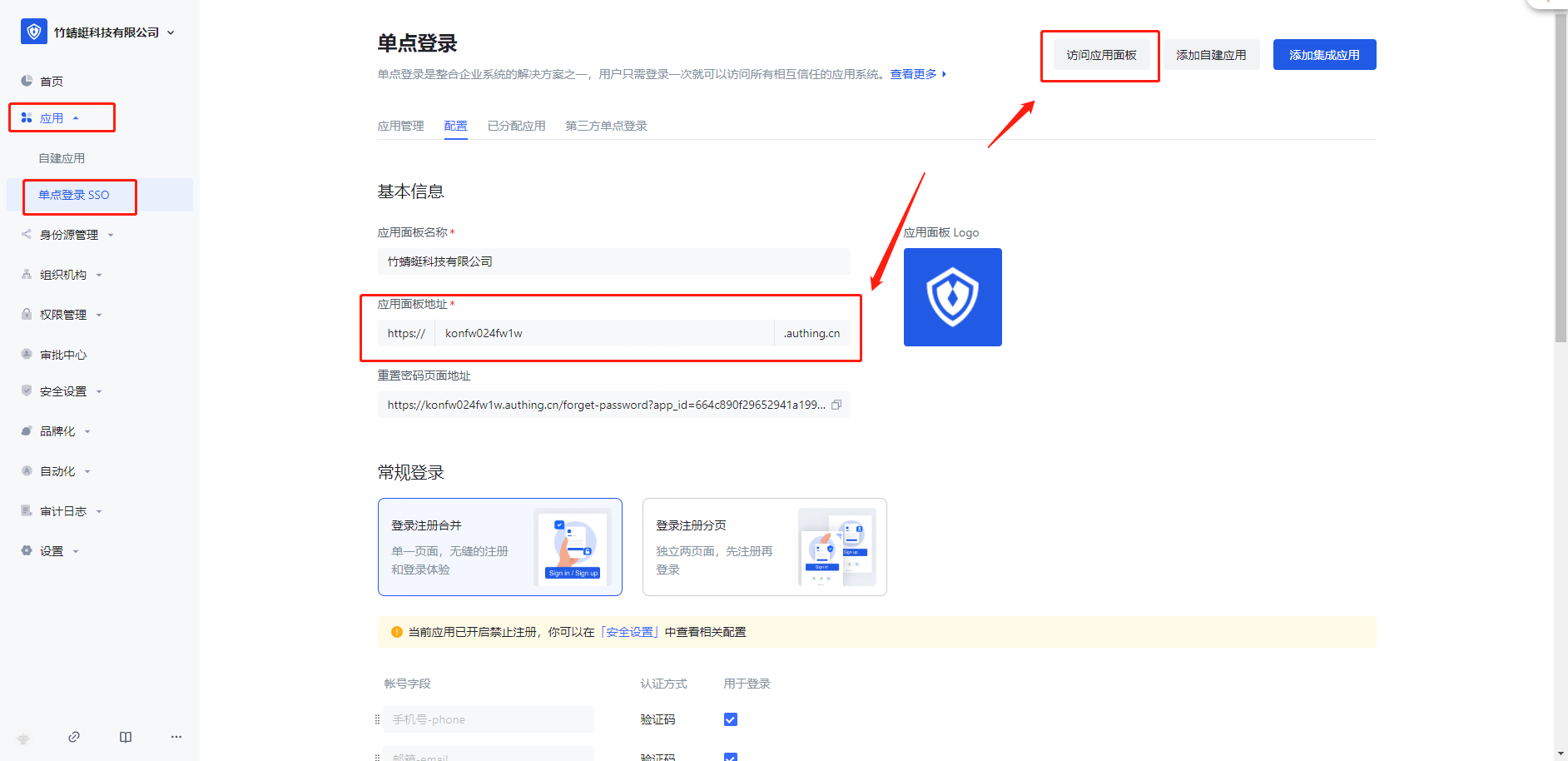
Visit https://cloud.fadada.com/work, enter the Settings - integration management - single sign-on (sso)
Add configuration and configure the above SAML application parameters:


Configuration mode: Manually enter configuration parameters (recommended), or upload the metadata in the IdP application
IdP SSO Address:... /saml2/sso (IdP Example 1)
IdP Public Key: MIIaux... o2NWV (IdP Example 2)
IdP Entity ID:.. /saml2/meta (IdP Example 3)
SAML Encryption algorithms: SHA-1, SHA-256 (recommended), SHA-512
Click Save to view the generated SP information:
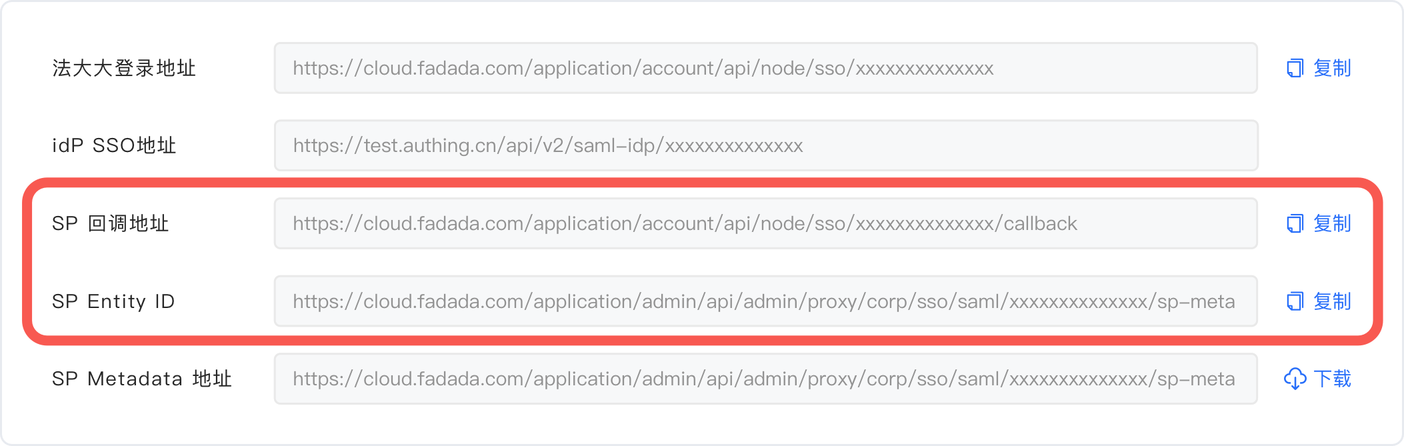

Method greatly login address: https://cloud.fadada.com/... /sso/xxxxxxxxxx (Example 1)
SP callback address: https://cloud.fadada.com/... /sso/xxxxxx/callback (Method large example 2)
SP Entity ID:https://cloud.fadada.com/... /sso/saml/x/sp-meta (Method large example 3)
Step 3: Access the IdP system and configure the above SP information to the SAML application
Configure SAML application ";Method Large Enterprise SSO (Example)"; and save:
Single sign-on address (ACS URL) :
https://cloud.fadada.com/... /sso/xxxxx/callback (Method large example 2)
Application unique ID (SP Entity ID) :
https://cloud.fadada.com/... /sso/saml/xxx/sp-meta (Method large example 3)
Application Account (Name ID) : Custom or application account (Recommended)
Authorization scope: Customized or accessible to all employees (Recommended)
Enable SAML application ";Method Large Enterprise SSO (Example)";
Step 4: Access the law, go to Enterprise Settings - Integrated management - Single sign-on,
After ensuring that your (operator's) member ID is the same as the IdP account, enable the single sign-on configuration
The OpenID Connent (OIDC) mode implements single sign-on (SSO)
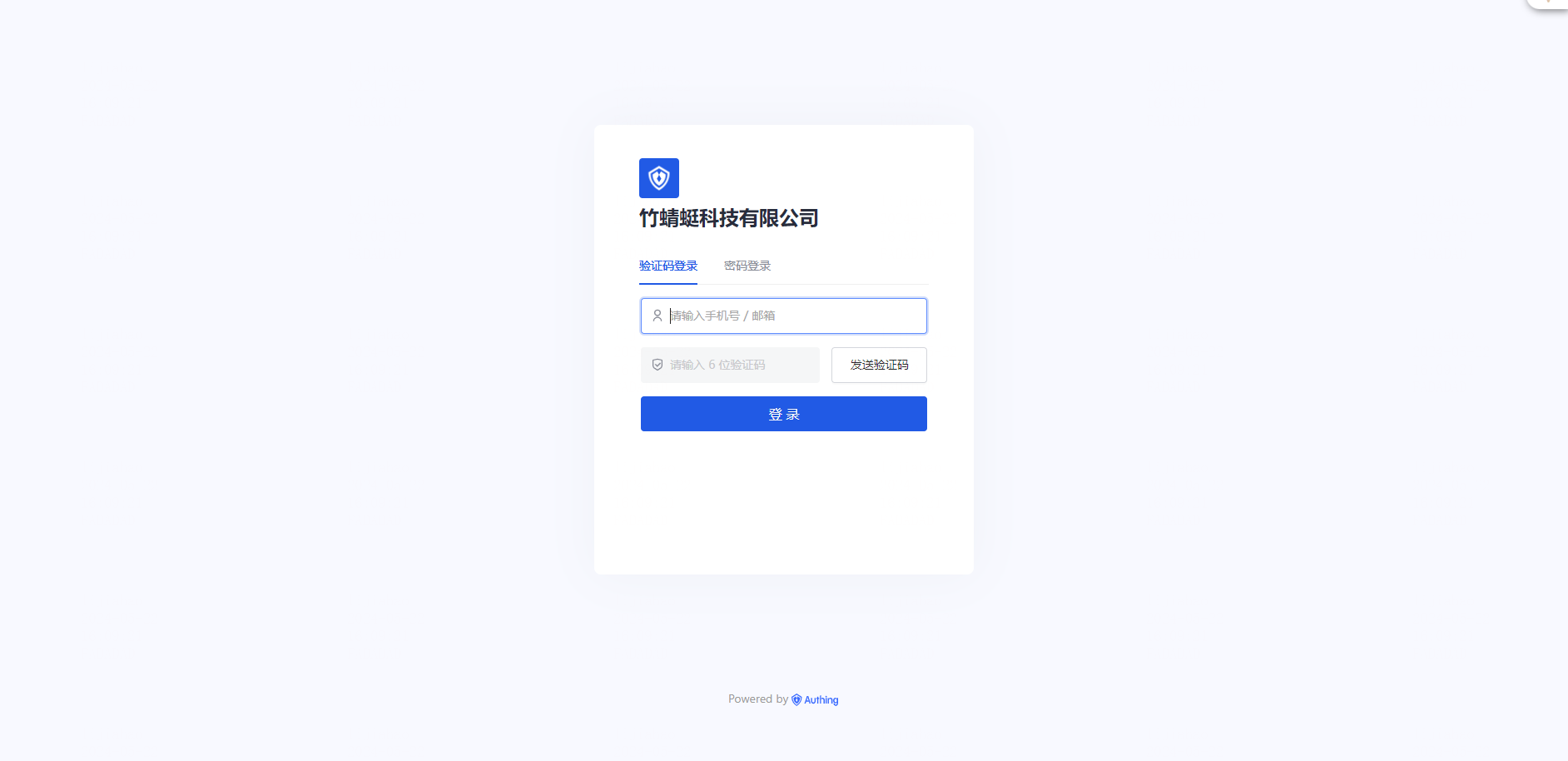
SSO login
Member login
1, jump from other systems login method is large
2. (or) Visit the Law School SSO login page
Access method greatly website: https://cloud.fadada.com/work, choose the SSO login, the login number input method of enterprise greatly. How to check the company's law size?

Q&A
Q: How many identity sources can I enable at the same time?
A: Currently, only one identity source can be enabled at a time. To use a new identity source, disable the original one.
Q: How to troubleshoot member login error?
A: Contact the super administrator or the administrator with organization management permission to confirm that the ID of the IdP member account is the same as the ID of the IDP member ID.